Manage Service Access and Security
As administrator, you manage access to your Oracle Analytics Cloud environment for your organization using security features in Oracle Cloud Infrastructure and Oracle Identity Cloud Service.
Topics
- Give Users Permissions to Manage Analytics Cloud Instances
- Give Data Sources Access to Analytics Cloud Instances
- Deploy Oracle Analytics Cloud with a Private Endpoint
- Connect to Private Data Sources Through a Private Access Channel
- Use Network Security Groups to Control Access
- Federate with Oracle Identity Cloud Service Manually
- Set Up a Custom Vanity URL
- Encrypt Sensitive Information
Give Users Permissions to Manage Analytics Cloud Instances
You can give other users permissions to manage Oracle Analytics Cloud instances through security polices.
About Permissions to Manage Oracle Analytics Cloud Instances
You use authorization policies to control access to resources in your tenancy. For example, you can create a policy that authorizes users to create and manage Oracle Analytics Cloud instances.
You create policies using the Oracle Cloud Infrastructure Console. For detailed information, see Managing Policies.
| Resource Types | Description |
|---|---|
|
analytics-instance |
A single Oracle Analytics Cloud instance. |
|
analytics-instances |
One or more Oracle Analytics Cloud instances. |
|
analytics-instance-work-request |
A single work request for Oracle
Analytics Cloud.
Each operation you perform on an Oracle Analytics Cloud instance, creates a work request. For example, operations such as create, start, stop, and so on. |
| analytics-instance-work-requests | One or more work requests. |
Supported Variables
The values of these variables are supplied by Oracle Analytics Cloud. In addition, other general variables are supported. See General Variables for All Requests.
| Variable | Type | Description | Sample Value |
|---|---|---|---|
| target.analytics-instance.id | ocid | OCID for the Analytics Cloud instance. | target.analytics-instance.id = 'oci1.analyticsinstance.oc1..abc123' |
| target.analytics-instance.name | string | Name of the Analytics Cloud instance. | target.analytics-instance.name = 'myanalytics_1' |
| target.analytics-instance.source-compartment.id | ocid | OCID of the source compartment, in a "move compartment" operation. | target.analytics-instance.source-compartment.id = 'ocid1.compartment.oc1..aaa100' |
| target.analytics-instance.destination-compartment.id | ocid | OCID of the destination compartment in a "move compartment" operation. | target.analytics-instance.destination-compartment.id = 'ocid1.compartment.oc1..aaa200' |
Details for Verb and Resource-Type Combinations
Oracle Cloud Infrastructure offers a standard set of verbs to define permissions across Oracle Cloud Infrastructure resources (Inspect, Read, Use, Manage). These tables list the Oracle Analytics Cloud permissions associated with each verb. The level of access is cumulative as you go from Inspect to Read to Use to Manage.
INSPECT
| Resource- Type | INSPECT Permission |
|---|---|
|
|
|
|
READ
| Resource- Type | READ Permission |
|---|---|
|
|
|
|
USE
| Resource- Type | USE Permission |
|---|---|
|
|
|
|
MANAGE
| Resource- Type | MANAGE Permission |
|---|---|
|
|
|
|
Permissions Required for Each API Operation
This table shows the API operations available for Oracle Analytics Cloud, grouped by resource type.
| REST API Operation | CLI Command Operation | Permission Required to Use the Operation |
|---|---|---|
| ListAnalyticsInstances | analytics-instance list | ANALYTICS_INSTANCE_INSPECT |
| CreateAnalyticsInstance | analytics-instance create | ANALYTICS_INSTANCE_CREATE |
| GetAnalyticsInstance | analytics-instance get | ANALYTICS_INSTANCE_READ |
| UpdateAnalyticsInstance | analytics-instance update | ANALYTICS_INSTANCE_UPDATE |
| DeleteAnalyticsInstance | analytics-instance delete | ANALYTICS_INSTANCE_DELETE |
| StartAnalyticsInstance | analytics-instance start | ANALYTICS_INSTANCE_USE |
| StopAnalyticsInstance | analytics-instance stop | ANALYTICS_INSTANCE_USE |
| ScaleAnalyticsInstance | analytics-instance scale | ANALYTICS_INSTANCE_MANAGE |
| ChangeAnalyticsInstanceCompartment | analytics-instance change-compartment | ANALYTICS_INSTANCE_MOVE |
| ChangeAnalyticsInstanceNetworkEndpoint | analytics-instance change-network-endpoint | ANALYTICS_INSTANCE_MANAGE |
| GetPrivateAccessChannel | analytics-instance get-private-access-channel | ANALYTICS_INSTANCE_MANAGE |
| CreatePrivateAccessChannel | analytics-instance create-private-access-channel | ANALYTICS_INSTANCE_MANAGE |
| UpdatePrivateAccessChannel | analytics-instance update-private-access-channel | ANALYTICS_INSTANCE_MANAGE |
| DeletePrivateAccessChannel | analytics-instance delete-private-access-channel | ANALYTICS_INSTANCE_MANAGE |
| CreateVanityUrl | analytics-instance create-vanity-url | ANALYTICS_INSTANCE_MANAGE |
| UpdateVanityUrl | analytics-instance update-vanity-url | ANALYTICS_INSTANCE_MANAGE |
|
DeleteVanityUrl |
analytics-instance delete-vanity-url | ANALYTICS_INSTANCE_MANAGE |
| SetKmsKey | analytics-instance set-kms-key | ANALYTICS_INSTANCE_MANAGE |
| ListWorkRequests | work-request list | ANALYTICS_INSTANCE_WR_INSPECT |
| GetWorkRequest | work-request get | ANALYTICS_INSTANCE_WR_READ |
| DeleteWorkRequest | work-request delete | ANALYTICS_INSTANCE_WR_DELETE |
| ListWorkRequestErrors | work-request-error list | ANALYTICS_INSTANCE_WR_INSPECT |
| ListWorkRequestLogs | work-request-log list | ANALYTICS_INSTANCE_WR_INSPECT |
Example Policy Statements to Manage Analytics Cloud Instances
Here are typical policy statements that you might use to authorize access to Oracle Analytics Cloud instances.
When you create a policy for your tenancy, you grant users access to all compartments by way of policy inheritance. Alternatively, you can restrict access to individual Oracle Analytics Cloud instances or compartments.
Let users in the Administrators group fully manage any Analytics instance
# Full manage permissions (Create, View, Update, Delete, Scale, Start, Stop...)
allow group Administrators to manage analytics-instances in tenancy
allow group Administrators to manage analytics-instance-work-requests in tenancyLet users in the analytics_power_users group read, start, and stop all Analytics instances in compartment MyOACProduction
# Use permissions (List, Get, Start, Stop)
allow group analytics_power_users to use analytics-instances in compartment MyOACProductionLet users in the analytics_test_users group create and manage a single Analytics instance (myanalytics_1) in compartment MyOACTest
# Full manage permissions on a single instance
allow group analytics_test_users to manage analytics-instances in compartment MyOACTest where target.analytics-instances.name = 'myanalytics_1'Let users in the analytics_power_users group move Analytics instances between two named compartments
# Custom permissions to move instances between two specific compartments.
allow group analytics_power_users to {ANALYTICS_INSTANCE_INSPECT, ANALYTICS_INSTANCE_READ, ANALYTICS_INSTANCE_MOVE} in tenancy
where all {
target.analytics-instance.source-compartment.id =
'ocid1.compartment.oc1..aaa100',
target.analytics-instance.destination-compartment.id =
'ocid1.compartment.oc1..aaa200'
}Let users in the analytics_users group inspect any Analytics instance and their associated work requests
# Inspect permissions (list analytics instances and work requests) using metaverbs.
allow group analytics_users to inspect analytics-instances in tenancy
allow group analytics_users to inspect analytics-instance-work-requests in tenancy# Inspect permissions (list analytics instances and work requests) using permission names.
allow group analytics_users to {ANALYTICS_INSTANCE_INSPECT} in tenancy
allow group analytics_users to {ANALYTICS_INSTANCE_WR_INSPECT} in tenancyLet users in the analytics_users2 group read details about any Analytics instance and their associated work requests
# Read permissions (read complete analytics instance and work request metadata) using metaverbs.
allow group analytics_users2 to read analytics-instances in tenancy
allow group analytics_users2 to read analytics-instance-work-requests in tenancy# Read permissions (read complete analytics instance and work request metadata) using permission names.
allow group analytics_users2 to {ANALYTICS_INSTANCE_INSPECT, ANALYTICS_INSTANCE_READ} in tenancy
allow group analytics_users2 to {ANALYTICS_INSTANCE_WR_INSPECT, ANALYTICS_INSTANCE_WR_READ} in tenancyLet users in the analytics_users2 group view performance metrics for any Analytics instance in a named compartment
# View performance metrics permissions
allow group analytics_users2 to read metrics in compartment myOACProduction Let users in the analytics_power_users2 group read, start, and stop all Analytics instances and read their associated work requests
# Use permissions (read, stop, start on analytics instance, read on work request) using metaverbs.
allow group analytics_power_users2 to use analytics-instances in tenancy
allow group analytics_power_users2 to read analytics-instance-work-requests in tenancy# Use permissions (read, stop, start on analytics instance, read on work request) using permission names.allow group
analytics_power_users2 to {ANALYTICS_INSTANCE_INSPECT, ANALYTICS_INSTANCE_READ, ANALYTICS_INSTANCE_USE} in
tenancy
allow group
analytics_power_users2 to {ANALYTICS_INSTANCE_WR_INSPECT, ANALYTICS_INSTANCE_WR_READ} in
tenancyLet users in the Administrators2 group manage any Analytics instance and their associated work requests
# Full manage permissions (use, scale, delete on analytics instance, read and cancel on work request) using metaverbs.
allow group Administrators2 to manage analytics-instances in tenancy
allow group Administrators2 to manage analytics-instance-work-requests in tenancy# Full manage permissions (use, create, scale, delete on analytics instance, read and cancel on work request) using permission names.allow group
Administrators2 to
{ANALYTICS_INSTANCE_INSPECT, ANALYTICS_INSTANCE_READ, ANALYTICS_INSTANCE_USE,
ANALYTICS_INSTANCE_CREATE, ANALYTICS_INSTANCE_DELETE, ANALYTICS_INSTANCE_UPDATE,
ANALYTICS_INSTANCE_MOVE, ANALYTICS_INSTANCE_MANAGE} in
tenancy
allow group
Administrators2 to
{ANALYTICS_INSTANCE_WR_INSPECT, ANALYTICS_INSTANCE_WR_READ, ANALYTICS_INSTANCE_WR_DELETE} in
tenancySet Up Polices (Identity Domains)
If your cloud account offers identity domains, use Oracle Cloud Infrastructure Identity and Access Management (IAM) to set up users and groups before you set up security policies in Oracle Cloud Infrastructure.
Typical Workflow for Setting Up Policies to Manage Analytics Cloud Instances (Identity Domains)
If you’re setting up policies for the first time, take some time to understand what's required before you start.
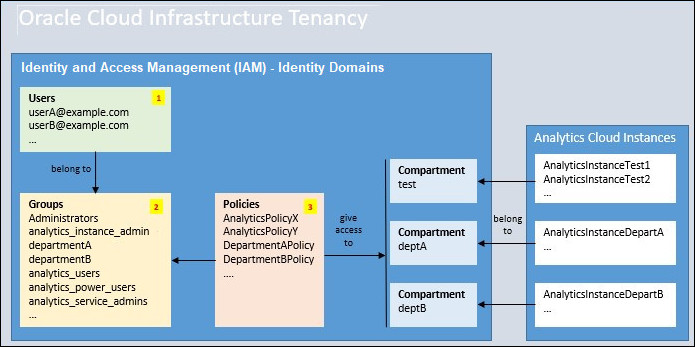
High-level steps:
- Use Oracle Cloud Infrastructure Identity and Access Management Identity Domains to create users.
- Create one or more groups and assign users to each group, as
required.
Give the groups suitable names. For example, prefix them with
analyticsand use a meaningful naming convention such as: analytics_instance_admin, analytics_service_admins, analytics_power_users, analytics_users, and so on. - Create one or more polices, as required.
Give users in the IAM groups suitable access permissions on compartments and Oracle Analytics Cloud instances.
For more detailed steps, see the next topic.
Give a User Permissions to Manage Analytics Cloud Instances (Identity Domains)
You can create security policies to give users in your IAM identity domain suitable access to Oracle Analytics Cloud instances in Oracle Cloud Infrastructure Console.
Users belonging to any groups mentioned in the policy statement get their new permission when they next sign in to the Console.
Set Up Policies (Federated Oracle Identity Cloud Service)
If your cloud account federates with Oracle Identity Cloud Service, you need to map your users and groups in Oracle Identity Cloud Service to users and groups in Oracle Cloud Infrastructure Identity and Access Management (IAM) before you set up policies in Oracle Cloud Infrastructure.
Typical Workflow to Set Up Policies to Manage Analytics Cloud Instances (Oracle Identity Cloud Service)
If your cloud account federates with Oracle Identity Cloud Service and you're setting up policies for the first time, take some time to understand what's required before you start.
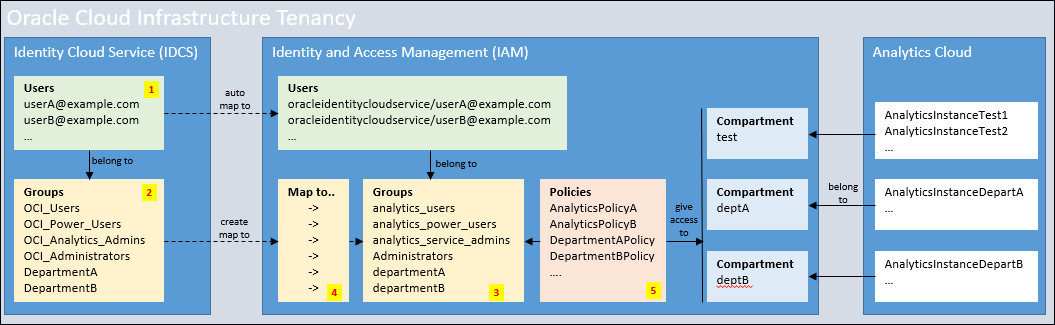
High-level steps:
- Create users in the federated Oracle Identity Cloud Service (IDCS).
- Create one or more groups and assign users to each group, as
required.
Give the groups suitable names and include only those users that you want to manage Oracle Analytics Cloud instances in Oracle Cloud Infrastructure (Gen 2). For example, prefix them with
OCIand indicate the level of access for users in the group: OCI_Users, OCI_Power_Users, OCI_Analytics_Admins, and so on. - Create groups in Oracle Cloud Infrastructure (OCI).
Give the groups suitable names. For example, prefix them with
analyticsand mirror the naming convention that you used in Oracle Identity Cloud Service: analytics_users, analytics_power_users, analytics_service_admins, and so on. - Map the groups you created in OCI to the groups in Oracle Identity Cloud Service.
- Create one or more polices, as required.
Give users in OCI groups suitable access permissions to compartments and Oracle Analytics Cloud instances.
For more detailed steps, see the next topic.
Give a User in Oracle Identity Cloud Service Permissions to Manage Analytics Cloud Instances
You can create security policies to give users in Oracle Identity Cloud Service suitable access to Oracle Analytics Cloud instances in Oracle Cloud Infrastructure Console.
- Sign-in to your cloud account as Cloud Account Administrator.
- Navigate to the federated Oracle Identity Cloud
Service.
- Click Identity & Security. Under Identity, click Federation.
- Click the link to your Oracle Identity Cloud Service Console.
- In Oracle Identity Cloud
Service, add one or more users.
- In the Users section, click Add a User.
- Enter details about the user, and click Finish.
- In Oracle Identity Cloud
Service, create one or more groups and assign users to the appropriate group.
- In Oracle Cloud
Infrastructure Console, create an OCI group that corresponds to each of the groups you
created in Oracle Identity Cloud
Service.
- Map OCI groups to the corresponding groups in Oracle Identity Cloud
Service.
- Create a policy that gives users belonging to an OCI group, specific access
permissions to Oracle
Analytics Cloud instances or compartments.
Users belonging to any groups mentioned in the policy statement get their new permission when they next sign in to the Console.
Give Data Sources Access to Analytics Cloud Instances
You can connect Oracle Analytics Cloud to a wide range of data sources. Some data sources, such as Oracle Autonomous Data Warehouse, require you to include the IP address of your Oracle Analytics Cloud instance in their allowlist.
Topics:
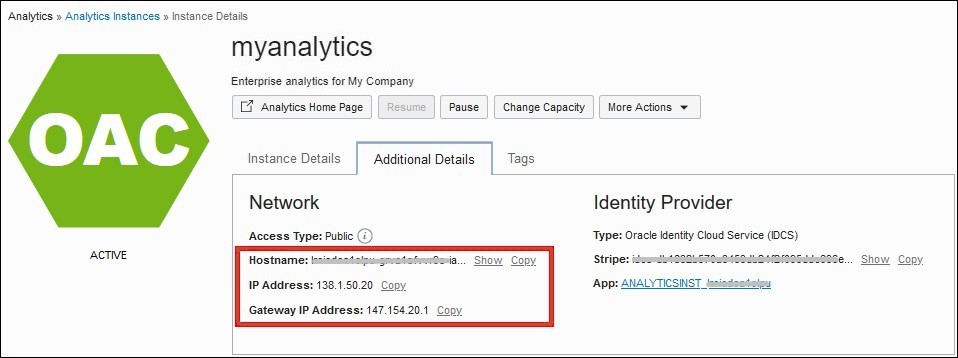
Find the IP Address or Host Name of Your Oracle Analytics Cloud Instance
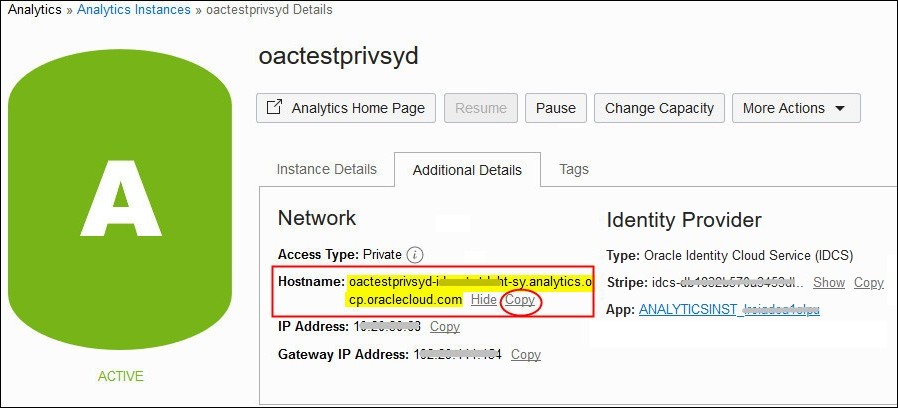
You can find the hostname and IP address information for your Oracle Analytics Cloud deployment on the Instance Details tab in Oracle Cloud Infrastructure Console.
You'll find this information useful for several scenarios.
- Gateway IP Address: Some data sources use an allowlist to control access to their data. To include your Oracle Analytics Cloud instance in an allowlist, copy the Gateway IP Address that is displayed on the Additional Details tab and add it to the allowlist so that Oracle Analytics Cloud can connect and access the data.
- IP Address: If you set up a vanity URL, you must add a DNS entry that maps the custom domain name you want to use to the IP Address of your Oracle Analytics Cloud instance.
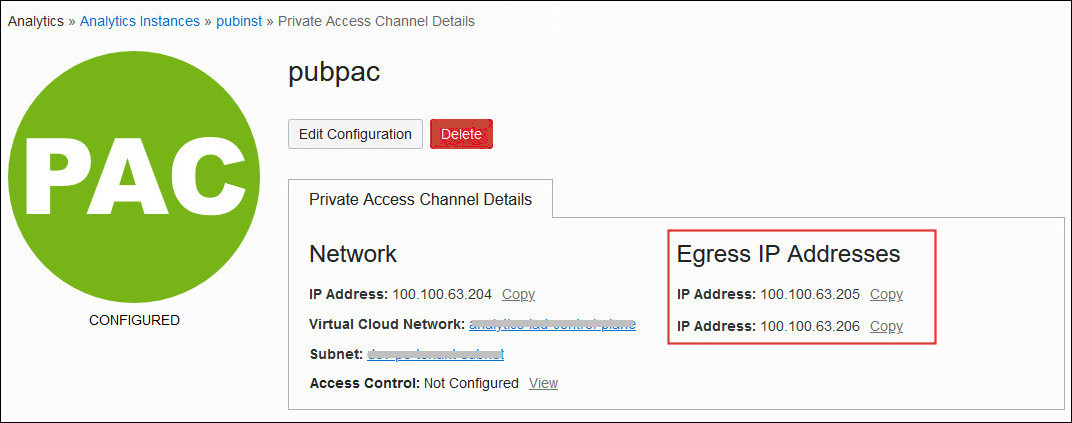
- Egress IP Addresses: If you set up a private access channel for Oracle Analytics Cloud, you can also find the egress IP addresses that Oracle Analytics Cloud uses to access private data sources. You copy the Egress IP Address information and add it to the allowlist for the private data source so that Oracle Analytics Cloud can connect and access the data.
Add the IP Address of Your Oracle Analytics Cloud Instance to Allowlists
Before you try to connect Oracle Analytics Cloud to an Oracle Cloud database, ask the database administrator to add the Gateway IP Address (or address range) for your Oracle Analytics Cloud instance to the target database's allowlist. The database administrator must add a security rule on the target Oracle Cloud database that allows TCP/IP traffic from Oracle Analytics Cloud on a specific database port.
This topic describes how to add Oracle Analytics Cloud to the allowlist for an Oracle Cloud database. If you want to connect to other data sources, follow similar steps, as required.
Public IP Ranges and Gateway IPs for Oracle Analytics Cloud Instances
If you want to connect Oracle Analytics Cloud with a public endpoint to a database in Oracle Cloud, you must add the public gateway IP Address (or IP address range) where your Oracle Analytics Cloud instance is located on Oracle Cloud Infrastructure to the database's allowlist.
The public IP address information that you provide depends on the type of database you want to connect to and whether or not your Oracle Analytics Cloud instance is deployed in the same region as the database.
| Database | Oracle Autonomous Data Warehouse | Oracle Autonomous Transaction Processing | Any Other Oracle Cloud Database |
|---|---|---|---|
| Same region as Oracle Analytics Cloud | Allow 240.0.0.0/4 |
Allow 240.0.0.0/4 |
Allow the region-specific IP address. |
| Different region to Oracle Analytics Cloud | Allow the region-specific IP address. | Allow the region-specific IP address. | Allow the region-specific IP address. |
Region-Specific Public IP Address Information for Oracle Analytics Cloud
Use Oracle Cloud Infrastructure Console to find the public gateway IP address (or IP address range) of your Oracle Analytics Cloud instance that you or your database administrator must add to the database's allowlist. See Find the IP Address or Host Name of Your Oracle Analytics Cloud Instance.
Alternatively, if you know the region where you deployed your Oracle Analytics Cloud instance, find that region in the table below and make a note of the public IP address information listed in the IP Address Range column or the Gateway IP Address column.
The security policy enforced by your company or organization determines whether you must provide the IP address ranges or Gateway IP address. If you're not sure, check with your network administrator.
For example, if you deployed your Oracle
Analytics Cloud instance in Tokyo, Japan East (ap-tokyo-1) and your company's security policy
requires you to provide an IP address range, you add
192.29.39.56/29. Alternatively, if you're required to provide a
Gateway IP address, you add 192.29.39.59.
| Region Where Oracle Analytics Cloud Deployed | Region Identifier | IP Address Range | Gateway IP Address |
|---|---|---|---|
| Asia Pacific (APAC) | |||
| Australia Southeast (Melbourne) | ap-melbourne-1 | 192.29.211.152/29 | 192.29.211.154 |
| Australia East (Sydney) | ap-sydney-1 | 192.29.144.152/29 | 192.29.144.154 |
| India South (Hyderabad) | ap-hyderabad-1 | 129.148.128.56/29 | 129.148.128.61 |
| India West (Mumbai) | ap-mumbai-1 | 192.29.48.240/29 | 192.29.48.246 |
| Japan Central (Osaka) | ap-osaka-1 | 192.29.242.208/29 | 192.29.242.211 |
| Japan East (Tokyo) | ap-tokyo-1 | 192.29.39.56/29 | 192.29.39.59 |
| Singapore (Singapore) | ap-singapore-1 | 129.148.178.96/29 | 129.148.178.102 |
| South Korea Central (Seoul) | ap-seoul-1 | 192.29.20.96/29 | 192.29.20.98 |
| South Korea North (Chuncheon) | ap-chuncheon-1 | 129.148.144.24/29 | 129.148.144.31 |
| Europe, the Middle East and Africa (EMEA) | |||
| France Central (Paris) | eu-paris-1 | 155.248.129.232/29 | 155.248.129.237 |
| France South (Marseille) | eu-marseille-1 | 129.149.99.160/29 | 129.149.99.166 |
| Germany Central (Frankfurt) | eu-frankfurt-1 |
147.154.148.0/29 138.1.64.32/29 147.154.131.128/29 |
147.154.148.171 138.1.64.33 147.154.131.133 |
| Israel 1 (Jerusalem) | il-jerusalem-1 | 129.149.121.32/29 | 129.149.121.32 |
| Italy Northwest (Milan) | eu-milan-1 | 129.149.113.56/29 | 129.149.113.56 |
| Netherlands Northwest (Amsterdam) | eu-amsterdam-1 |
192.29.193.72/29 |
192.29.193.76 |
| Saudi Arabia West (Jeddah) | me-jeddah-1 | 192.29.225.72/29 | 192.29.225.78 |
| Serbia (Jovanovac) | eu-jovanovac-1 | 207.127.84.72/29 | 207.127.84.75 |
| South Africa Central (Johannesburg) | af-johannesburg-1 | 129.149.67.184/29 | 129.149.67.187 |
| Spain Central (Madrid) | eu-madrid-1 | 155.248.138.136/29 |
155.248.138.140 |
| Sweden Central (Stockholm) | eu-stockholm-1 | 129.149.80.152/29 | 129.149.80.153 |
| Switzerland North (Zurich) | eu-zurich-1 | 192.29.60.112/29 | 192.29.60.112 |
| UAE Central (Abu Dhabi) | me-abudhabi-1 | 129.149.50.80/29 | 129.149.50.84 |
| UAE East (Dubai) | me-dubai-1 | 129.148.214.184/29 | 129.148.214.189 |
| UK South (London) | uk-london-1 |
147.154.229.168/29 147.154.232.168/29 |
147.154.229.170 147.154.232.175 |
| UK West (Newport) | uk-cardiff-1 |
129.149.20.112/29 |
129.149.20.118 |
| Latin America | |||
| Brazil East (Sao Paulo) | sa-saopaulo-1 | 192.29.128.232/29 | 192.29.128.238 |
| Brazil Southeast (Vinhedo) | sa-vinhedo-1 | 129.149.2.208/29 | 129.149.2.208 |
| Chile Central (Santiago) | sa-santiago-1 | 129.148.152.208/29 | 129.148.152.214 |
| Chile Central (Valparaiso) | sa-valparaiso-1 | 10.23.0.0/16 | 165.1.96.225 |
| Colombia (Bogota) | sa-bogota-1 | 10.24.0.0/16 | 158.247.99.174 |
| Mexico Central (Monterrey) | mx-monterrey-1 | 139.177.105.88/29 | 139.177.105.94 |
| Mexico Central (Queretaro) | mx-queretaro-1 | 155.248.146.152/29 | 155.248.146.152 |
| North America | |||
| Canada Southeast (Montreal) | ca-montreal-1 | 192.29.82.176/29 | 192.29.82.176 |
| Canada Southeast (Toronto) | ca-toronto-1 |
192.29.13.0/29 192.29.14.104/29 |
192.29.13.6 192.29.14.106 |
| US East (Ashburn) | us-ashburn-1 |
147.154.20.0/29 147.154.3.184/29 147.154.0.0/29 147.154.3.8/29 130.35.99.216/29 147.154.16.168/29 |
147.154.20.1 147.154.3.185 147.154.0.3 147.154.3.13 130.35.99.221 147.154.16.169 |
| US North (Chicago) | us-chicago-1 | 131.186.10.104/29 | 131.186.10.109 |
| US West (Phoenix) | us-phoenix-1 |
147.154.104.160/29 138.1.32.24/29 147.154.120.80/29 |
147.154.104.165 138.1.32.29 147.154.120.84 |
| US West (San Jose) | us-sanjose-1 |
129.148.161.112/29 |
129.148.161.117 |
Restrict Access to Oracle Analytics Cloud Deployed with a Public Endpoint
If you deploy Oracle Analytics Cloud with a public internet accessible endpoint, you can restrict access through one or more rules.
Topics:
About Public Endpoints and Access Control Rules
When you set up an Oracle Analytics Cloud instance you have the option to deploy Oracle Analytics Cloud with a public internet accessible endpoint.
For security reasons, you might want to restrict incoming traffic (ingress) through one or more access control rules. Similarly, if you use a private access channel to connect to private data sources, you might want to restrict outgoing traffic (egress) through one or more network security group rules.
Ingress Access Control Rules
- A specific set of IP addresses
- CIDR block ranges (Classless Inter-Domain Routing)
- One or more Oracle Cloud Infrastructure VCNs (Virtual Cloud Network)
- Oracle services in the same region through a service gateway
- Any combination of the above, that is, IP addresses, CIDR ranges, VCNs, Oracle services.
For example:
- Scenario 1 - Allow access to Oracle Analytics Cloud over the public internet. Restrict access to a fixed set of IP addresses.
-
Scenario 2 - Allow access to Oracle Analytics Cloud over the public internet. Restrict access to hosts within a fixed CIDR block range.
-
Scenario 3 - Allow access to Oracle Analytics Cloud from an Oracle Cloud Infrastructure VCN that's deployed in the same region as Oracle Analytics Cloud, without going over the public internet. At the same time, allow other third-party cloud services or users to access Oracle Analytics Cloud over the public internet.
- Scenario 4 - Allow access to Oracle Analytics Cloud from your on-premise network without going through the public internet. At the same time, allow other third-party cloud services or users to access Oracle Analytics Cloud over the public internet.
-
Scenario 6 - Allow access to Oracle Analytics Cloud from your on-premise network without going through the public internet. At the same time, allow Oracle Services in the same region to access Oracle Analytics Cloud.
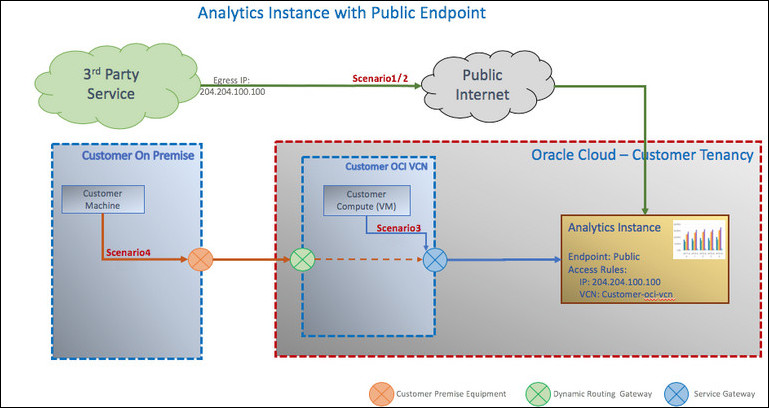
The sample diagram shows Oracle
Analytics Cloud deployed with a public endpoint and two access control rules. The
first rule allows access from the IP address
204.204.100.100 and the second rule allows
access from the Oracle Cloud Infrastructure VCN
customer-oci-vcn. The VCN is peered to an
on-premise network, and access to Oracle
Analytics Cloud is routed through the VCN's service gateway.
While Oracle
Analytics Cloud is accessible from the public internet, you can implement your
own access control rules to provide any additional security that you
need. In this example, only the third-party service with the egress
gateway IP address 204.204.100.100 accesses Oracle
Analytics Cloud over the public internet. Traffic from the on-premise network
never uses the public internet, instead it uses the service gateway
configured inside the VCN.
Egress Network Security Group Rules
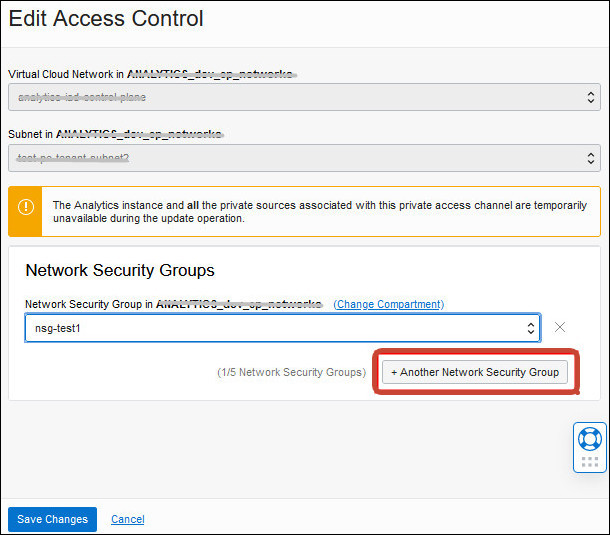
if your Oracle Analytics Cloud instance uses a private access channel to connect to private data sources, you can restrict outgoing traffic (egress) through one or more network security group rules. You can specify up to five network security group rules for the private channel and edit them whenever you want.
Prerequisites for a Public Endpoint
Before you create an Oracle Analytics Cloud instance that's accessible from the public internet, consider whether or not your organization wants to restrict incoming traffic (ingress).
No Restrictions
No prerequisites. If you want Oracle Analytics Cloud to be accessible from anywhere, you can create the Oracle Analytics Cloud instance with no access control.
Restrict Access to a Specific IP Address or CIDR Block Range
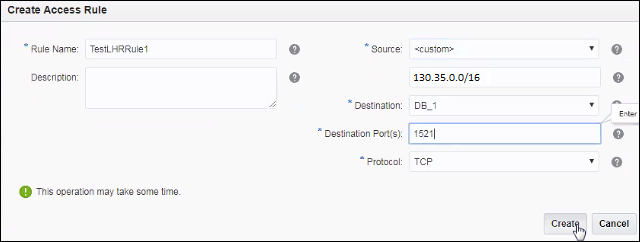
If you plan to limit incoming traffic (ingress) from a specific IP address or CIDR block range, record all the IP addresses or CIDR ranges that you want to allow. When you create your Oracle Analytics Cloud instance, you use this information to define one or more access control rules for Oracle Analytics Cloud.
Restrict Access to a Specific VCN
If you plan to limit access to traffic from a specific Oracle Cloud Infrastructure VCN, ensure that the VCN exists and you have the required policies to access the VCN.
-
Set up an Oracle Cloud Infrastructure VCN in the same region as the Oracle Analytics Cloud instance you plan to create.
-
Set up a service gateway in your VCN, and a route table to send traffic to Oracle Analytics Cloud through the service gateway.
-
Ensure that you (or whoever plans to create the Oracle Analytics Cloud instance) have the required policies to access the VCN.
-
READ policy for the compartment:
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ compartments IN TENANCY -
READ policy for the VCN:
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ virtual-network-family IN TENANCY
-
READ policy for the compartment:
Restrict Access to Oracle Services
No prerequisites. After creating your instance, you can add a single access control rule that allows all trusted Oracle Services in your region to access your Oracle Analytics Cloud instance.
Typical Workflow to Restrict Public Access using Rules
If you want to deploy an Oracle Analytics Cloud instance with a public endpoint for the first time with one or more access control rules, follow these tasks as a guide.
| Task | Description | More Information |
|---|---|---|
| Understand prerequisites for a public endpoint | Consider whether or not your organization plans to restrict access for incoming traffic. If required, record the IP addresses, CIDR ranges, and VCNs that you plan to allow access to. | Prerequisites for a Public Endpoint |
|
Create Oracle Analytics Cloud with a public endpoint |
Use Oracle Cloud Infrastructure Console to deploy a new service. |
|
|
Allow access by IP address, CIDR range, VCN, and to Oracle services |
Add one or more access control rules for incoming traffic. You can allow access to Oracle Analytics Cloud by public IP address, public CIDR block range, VCN, and to Oracle services. |
|
|
(Optional) Set up private access from your on-premise network |
Set up an Oracle Cloud Infrastructure VCN that connects to your on-premise network using FastConnect private peering or VPN Connect. The VCN must be deployed in the same region as Oracle Analytics Cloud. Set up a service gateway in your VCN, and a route table to send traffic to Oracle Analytics Cloud through the service gateway. Add an access control rule in your Oracle Analytics Cloud instance that allows access from your VCN. Configure VCN peering to your on-premise network through FastConnect or VPN Connect to enable access from your on-premise network. Configure transit routing with the VCN to give your on-premise network private access to Oracle Analytics Cloud. |
Setting Up a Service Gateway in the Console Control Incoming Traffic for a Public Endpoint (Ingress) |
|
(Optional) Set up private access from hosts on your VCN |
Set up an Oracle Cloud Infrastructure VCN in the same region as Oracle Analytics Cloud. Set up a service gateway in your VCN, and a route table to send traffic to Oracle Analytics Cloud through the service gateway. Add an access control rule in your Oracle Analytics Cloud instance that allows access from your VCN. |
|
|
(Optional) Set up a private access channel |
Set up a private access channel and register the domain names or
SCAN host names of the data sources that require private access.
Use network security group rules to restrict access to your private data sources. |
Connect to Private Data Sources Through a Private Access Channel |
Create Oracle Analytics Cloud with a Public Endpoint
You can use Oracle Cloud Infrastructure Console, API, or command line to deploy Oracle Analytics Cloud with a public endpoint.
This topic highlights the information you must configure to enable access over the public internet and define any access control rules that you require.
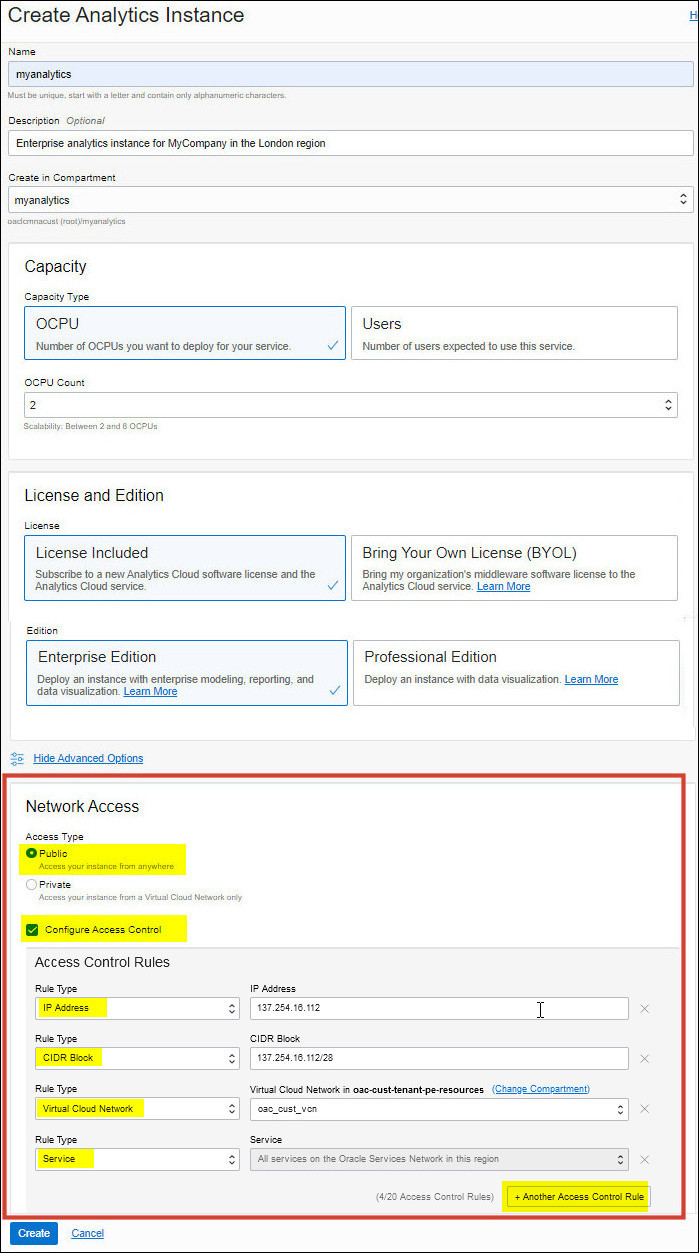
Control Incoming Traffic for a Public Endpoint (Ingress)
If you deployed Oracle Analytics Cloud with a public internet accessible endpoint, you can restrict incoming traffic to your service through an access control list (ACL) that contains one or more rules. You can add and edit access control rules whenever you want and allow access by public IP address, public CIDR block range, VCN, or other Oracle services using the Console, API, or command line.
Oracle Analytics Cloud enables you to specify up to 20 access rules.
Alternatively, if you're able to route traffic through a VCN, you can specify a single access rule in Oracle Analytics Cloud for the VCN and define all your access restrictions in the VCN instead.
Required IAM Policy to Edit Analytics Instance
Verb: manage
Resource Types: analytics-instance,
analytics-instances
Permission: ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Additional IAM Policy Required to Edit a Public Endpoint
Verb: read
Resource Type: virtual-network-family,
compartment, compartments
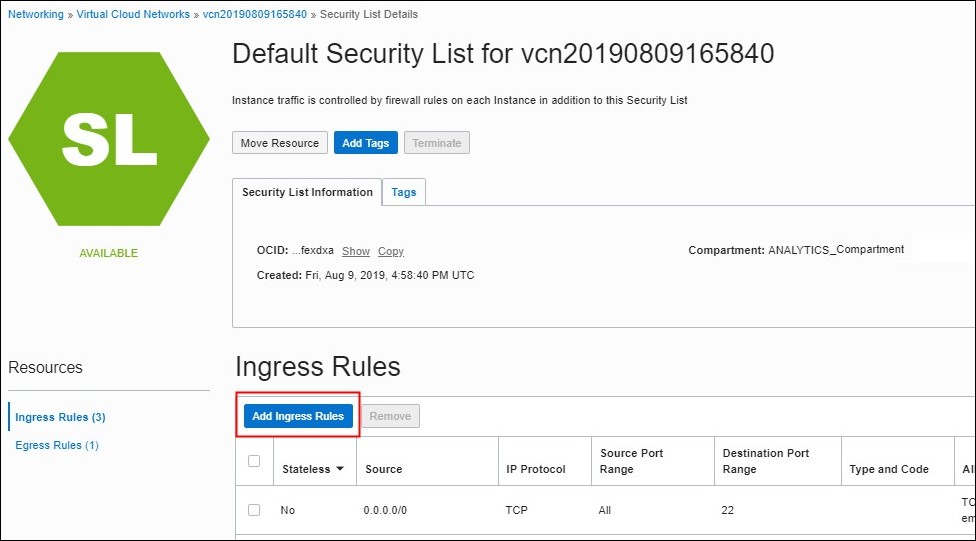
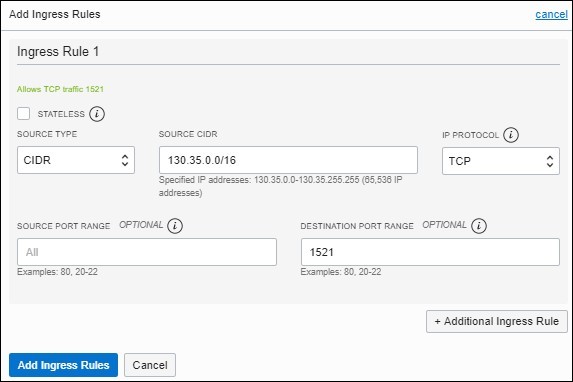
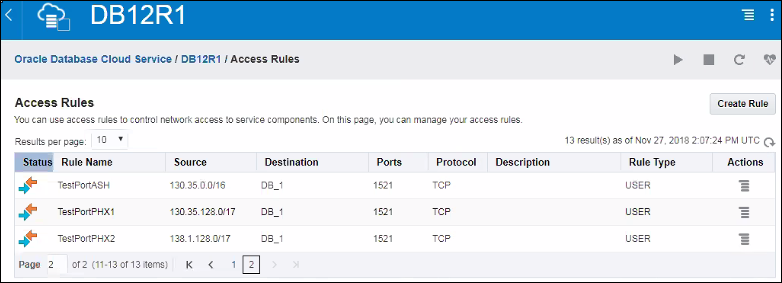
Manage Ingress Access Rules for a Public Endpoint using the Console
If you deployed Oracle Analytics Cloud with a public internet accessible endpoint, you can restrict incoming traffic to your service through an access control list (ACL) that contains one or more ingress rules. You can add and edit access control rules whenever you want and allow access to a public IP address, a public CIDR block range, a VCN or Oracle services.
Manage Ingress Access Rules for a Public Endpoint using the REST API
You can use the ChangeAnalyticsInstanceNetworkEndpoint
operation to change access control rules for incoming traffic to an Oracle
Analytics Cloud instance with a public endpoint.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Manage Ingress Access Rules for a Public Endpoint using the Command Line
You can use the change-network-endpoint command to change
access control rules for incoming traffic to an Oracle
Analytics Cloud instance with a public endpoint.
Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command:
Control Outgoing Traffic for a Public Endpoint (Egress)
If you deployed Oracle Analytics Cloud with a public internet accessible endpoint and you have private data sources that Oracle Analytics Cloud connects to over a private access channel, you can use egress rules that you define in network security groups to restrict outgoing traffic through the channel. You can add up to five network security groups using the Console, REST API, and CLI.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Verb: manage
Resource Type:
virtual-network-family
Verb: read
Resource Type: compartment,
compartments
Verb: use
Resource Type:
network-security-groups
To learn about other, more detailed access policy options, see Prerequisites for a Private Access Channel.
Deploy Oracle Analytics Cloud with a Private Endpoint
If you want only hosts within your virtual cloud network (VCN) or your on-premise network to have access to Oracle Analytics Cloud, you can deploy your Oracle Analytics Cloud instance with a private endpoint.
Topics:
- About Private Endpoints
- Prerequisites for a Private Endpoint
- Typical Workflow to Deploy Oracle Analytics Cloud with a Private Endpoint
- Create Oracle Analytics Cloud with a Private Endpoint
- Change a Private Endpoint using the Console
- Connect to Your On-premise Network using FastConnect or VPN Connect
About Private Endpoints
When you set up an Oracle Analytics Cloud instance you have the option to restrict access through a private endpoint. Private access means that traffic doesn't go over the internet. Private access can be from hosts within your virtual cloud network (VCN) or your on-premise network.
For example:
-
Scenario 1 - Allow access to Oracle Analytics Cloud from an on-premise (corporate) network. Don't allow access to anyone outside the corporate network.
- Scenario 2 - Allow access to Oracle Analytics Cloud from an Oracle Cloud Infrastructure VCN that's deployed in the same region as Oracle Analytics Cloud. Don't allow access to anyone outside the virtual cloud network.
When you deploy an Oracle Analytics Cloud instance with a private endpoint, the Oracle Analytics Cloud URL is only accessible from a browser if the client machine supports host name resolution. This means you must configure Domain Name Server (DNS) resolution on your private network to access the private endpoint. For example, you might use a DNS resolution strategy similar to that described in the article Hybrid DNS Configuration using DNS VM in VCN.
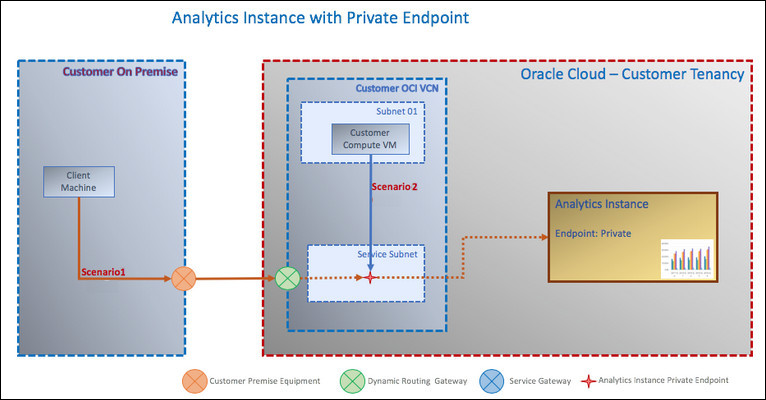
The diagram shows Oracle Analytics Cloud deployed with a private endpoint. The private Oracle Analytics Cloud is only accessible through an Oracle Cloud Infrastructure VCN in your tenancy; you can't access Oracle Analytics Cloud from the public internet.
You must peer the VCN to your on-premise network. To enable access to Oracle Analytics Cloud, the on-premise network DNS must provide host name resolution for Oracle Analytics Cloud.
Ingress and Egress Access Control Rules
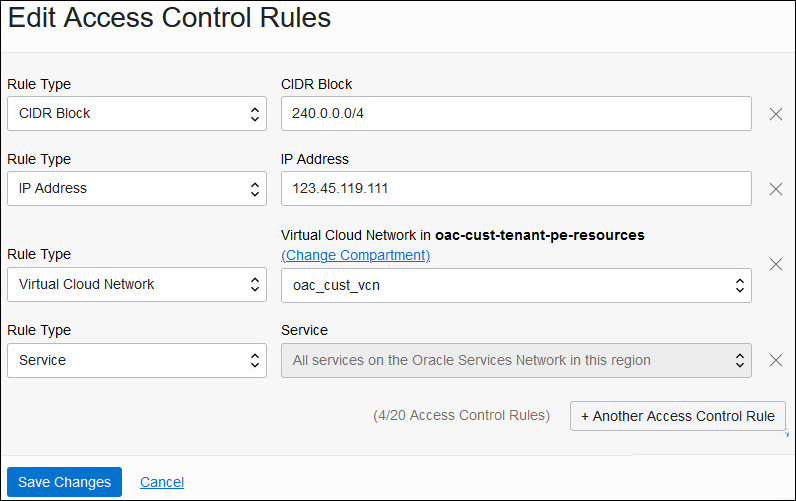
If you deploy Oracle Analytics Cloud with a private endpoint, you can restrict incoming traffic (ingress) to your service through predefined network security groups that contain one or more access rules.
If the Oracle Analytics Cloud uses a private access channel to connect to private data sources, you can also use network security groups to restrict outgoing traffic (egress) on the private access channel.
You can specify up to five network security group rules for incoming traffic and for outgoing traffic on the private access channel, and you can edit the rules whenever you want.
Prerequisites for a Private Endpoint
Before you create an Oracle Analytics Cloud instance with a private endpoint, complete the required prerequisites.
The prerequisites are the same for both scenarios:
- Private access from an on-premise network through an Oracle Cloud Infrastructure VCN
- Private access from hosts in an Oracle Cloud Infrastructure VCN
Typical Workflow to Deploy Oracle Analytics Cloud with a Private Endpoint
If you want to deploy an Oracle Analytics Cloud instance with a private endpoint for the first time, follow these tasks as a guide.
| Task | Description | More Information |
|---|---|---|
| Understand prerequisites for a private endpoint |
Set up an Oracle Cloud Infrastructure virtual cloud network (VCN) with a subnet for Oracle Analytics Cloud. The VCN must be in the region where you plan to deploy Oracle Analytics Cloud. |
Prerequisites for a Private Endpoint |
|
Create Oracle Analytics Cloud with a private endpoint |
Use Oracle Cloud Infrastructure Console to deploy a new service. |
|
| Configure the connection to your on-premise network using FastConnect or VPN Connect. |
(Only required if you want to access Oracle Analytics Cloud from an on-premise network) Use FastConnect or VPN to peer your on-premise network with the Oracle Cloud Infrastructure VCN through which you plan to access Oracle Analytics Cloud. |
Connect to Your On-premise Network using FastConnect or VPN Connect |
|
Change the VCN or subnet used to access Oracle Analytics Cloud |
If you want to access Oracle Analytics Cloud through a different VCN or subnet, you can edit the configuration at any time. |
|
|
(Optional) Control incoming traffic (ingress) and outgoing traffic (egress) using network security group rules |
Use one or more network security groups to control access to and from Oracle Analytics Cloud. |
Control Incoming and Outgoing Traffic for a Private Endpoint (Ingress and Egress) |
|
(Optional) Set up a private access channel |
Set up a private access channel and register the domain names or
SCAN host names of the data sources that require private access.
Optionally, use network security group rules to restrict traffic to and from your private data sources. |
Connect to Private Data Sources Through a Private Access Channel Control Incoming and Outgoing Traffic for a Private Endpoint (Ingress and Egress) |
Create Oracle Analytics Cloud with a Private Endpoint
You can use Oracle Cloud Infrastructure Console, API, or command line to deploy Oracle Analytics Cloud with a private endpoint.
This topic highlights the information you must configure to enable private access through a private endpoint.
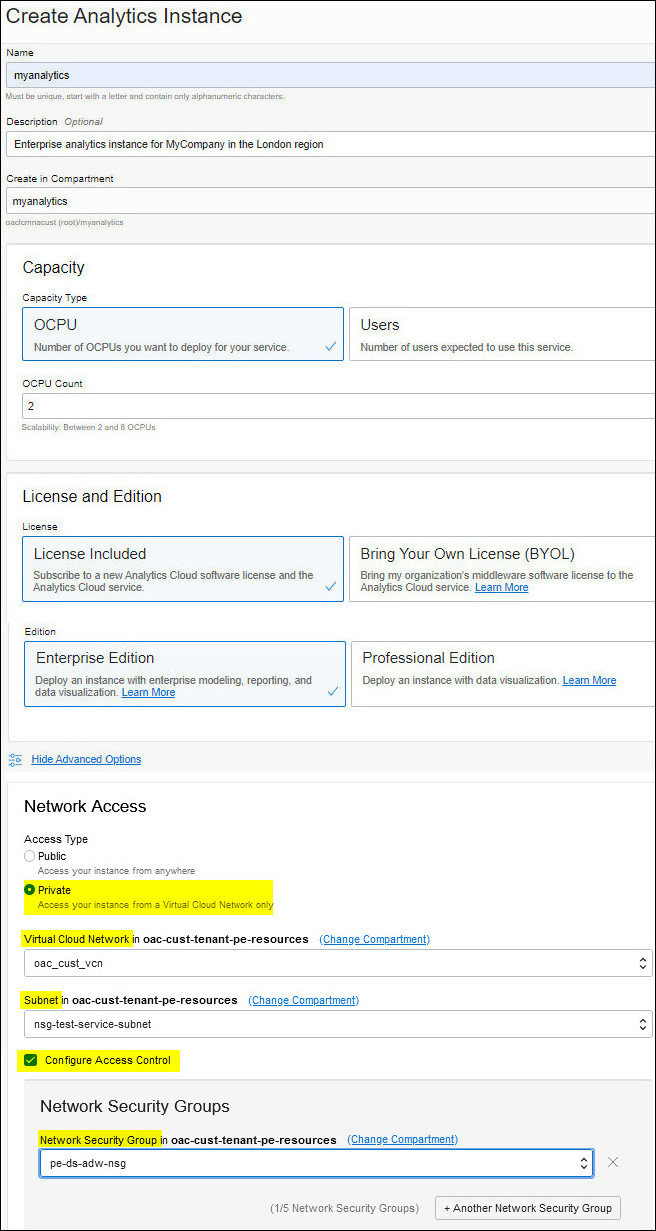
Connect to Your On-premise Network using FastConnect or VPN Connect
If you want to access an Oracle Analytics Cloud instance that is deployed with a private endpoint in an Oracle Cloud Infrastructure VCN from your on-premise network, you must peer your on-premise network with the Oracle Cloud Infrastructure VCN. You can use FastConnect or VPN to peer your on-premise network with a VCN on Oracle Cloud Infrastructure.
Typically, these tasks are performed by the network administrator responsible for the on-premise network and the Oracle Cloud Infrastructure network. You can complete these steps before or after you create your Oracle Analytics Cloud instance.
Change the VCN or Subnet Used to Access a Private Endpoint
If you want to access Oracle Analytics Cloud through a different VCN or subnet, you can edit the configuration using the Console, API, or command line.
Required IAM Policy to Edit Analytics Instance
Verb: manage
Resource Types:
analytics-instance,
analytics-instances
Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
IAM Policy Required to Change a Private Endpoint
Verb: manage
Resource Type: virtual-network-family
Verb: read
Resource Type: compartment,
compartments
To learn about other, more detailed access policy options, see Prerequisites for a Private Endpoint.
Change a Private Endpoint using the Console
If you want to access Oracle Analytics Cloud through a different VCN or subnet you can edit the configuration. You can also configure the network security groups used to control ingress and egress.
If you change the VCN you must reconfigure the network security groups.
Change a Private Endpoint using the REST API
You can use the ChangeAnalyticsInstanceNetworkEndpoint
operation to command to change the VCN or subnet used to access an Oracle
Analytics Cloud instance with a private endpoint.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Change a Private Endpoint using the Command Line
You can use the change-network-endpoint command to change
the VCN or subnet used to access an Oracle
Analytics Cloud instance with a private endpoint.
oci \
analytics analytics-instance change-network-endpoint \
--analytics-instance-id ocid1.analyticsinstance.oc1.us-ashburn-1.aaaaaaaa5pynfxr2e6wpshkhkoajoiqizwmhc6x7ogp4aw66whyq76fdk32q \
--network-endpoint-details '{
"networkEndpointType": "PRIVATE", "vcnId" :
"ocid1.vcn.oc1.us-ashburn-1.amaaaaaarfop2rqav4x2wox6dt72o57jmnevpguq63gcsdtrbk42bvz446sa",
"subnetId": "ocid1.subnet.oc1.us-ashburn-1.aaaaaaaal5xb6vodov35nbcqhsnwoypeieowgy44vambmnokzpwv22pvjxoq"
}'Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command:
Control Incoming and Outgoing Traffic for a Private Endpoint (Ingress and Egress)
If you deployed Oracle Analytics Cloud with a private endpoint, you can restrict incoming and outgoing traffic to your service through ingress and egress rules that you define in network security groups.
Oracle Analytics Cloud enables you to specify up to 5 network security groups and you can configure these network security groups at any time.
Required IAM Policy to Edit Analytics Instance
Verb: manage
Resource Types: analytics-instance,
analytics-instances
Permission: ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Additional IAM Policy Required to Edit a Private Endpoint
Verb: manage
Resource Type: virtual-network-family
Verb: read
Resource Type: compartment,
compartments
Verb: use
Resource Type:
network-security-groups
Connect to Private Data Sources Through a Private Access Channel
If the data you want to analyze is stored on a private host, you can set up a private access channel between your Oracle Analytics Cloud instance and your data source.
Topics:
About Private Access Channels
If you want Oracle Analytics Cloud to access data on a private host, you can set up a private access channel. A private access channel can give Oracle Analytics Cloud access to private data sources within your virtual cloud network (VCN) on Oracle Cloud Infrastructure or other networks peered to the VCN such as your corporate network.
You can set up a private access channel for Oracle Analytics Cloud instances deployed with Enterprise Edition. Private access channels aren't available to Oracle Analytics Cloud instances with Professional Edition.
Private access channels enable you to connect to private data source hosts. You can't use a private access channel to access any other type of private host. For example, you can't use private access channels to access private hosts that represent FTP servers, SMTP servers, printers , MapViewer configuration, or any other type of private host you might you use.
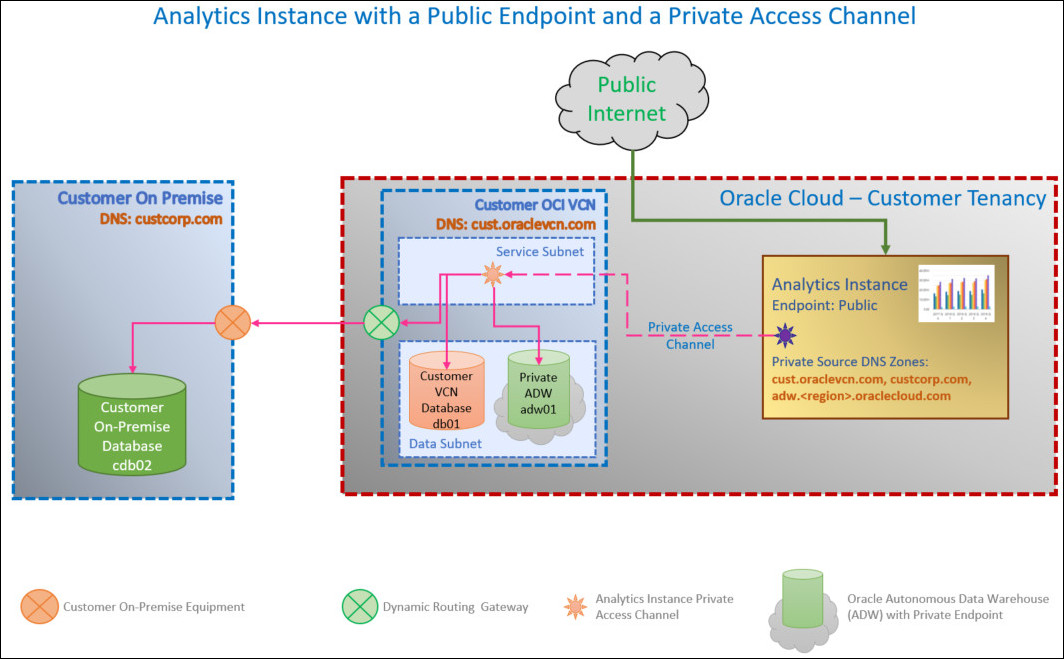
Private Access Channel for Oracle Analytics Cloud Instances with Public Endpoint
If Oracle Analytics Cloud has a public endpoint you must specify the VCN and subnet you want the private access channel to use.
If you want to restrict outgoing traffic (egress) over the private access channel, you can configure network security groups for your Oracle Analytics Cloud instance that contain one or more egress rules.
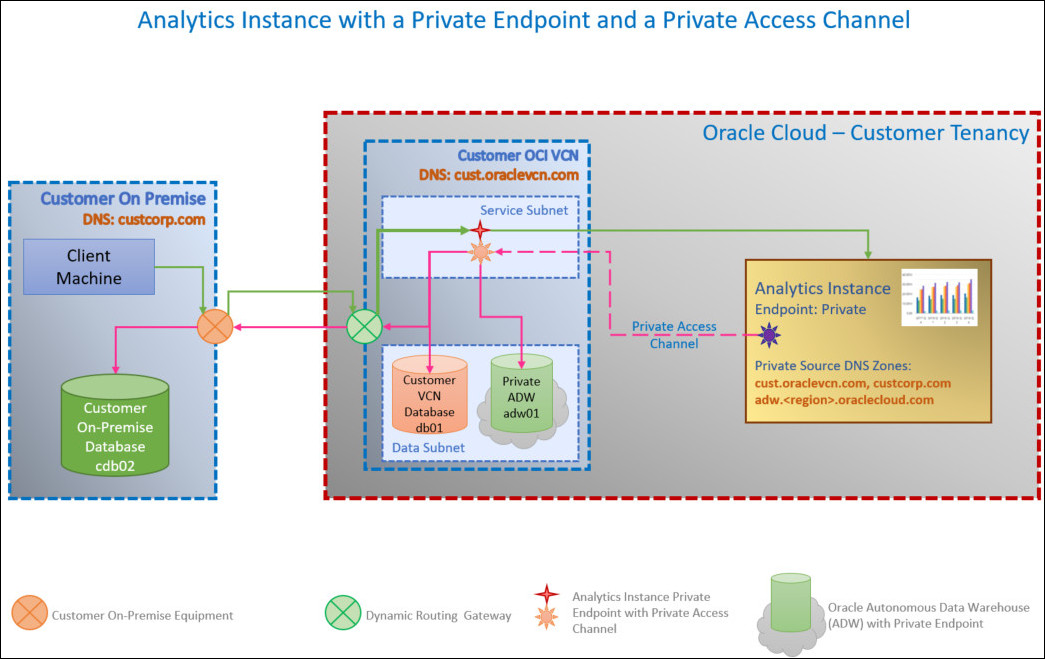
Private Access Channel for Oracle Analytics Cloud Instances with Private Endpoint
If Oracle Analytics Cloud has a private endpoint, the private access channel uses the same VCN and subnet as the private endpoint.
If you want to restrict incoming traffic (ingress) or outgoing traffic (egress) over the private access channel, you can configure network security groups for your Oracle Analytics Cloud instance that contain one or more ingress or egress rules.
About Private Data Sources
Oracle Analytics Cloud can access private data sources with a Fully Qualified Domain Name (FQDN) that resolves through the Domain Name System (DNS) in your tenancy. Oracle Analytics Cloud can also access private Oracle Databases configured with a Single Client Access Name (SCAN).
- DNS Zone: Specify domain names such as
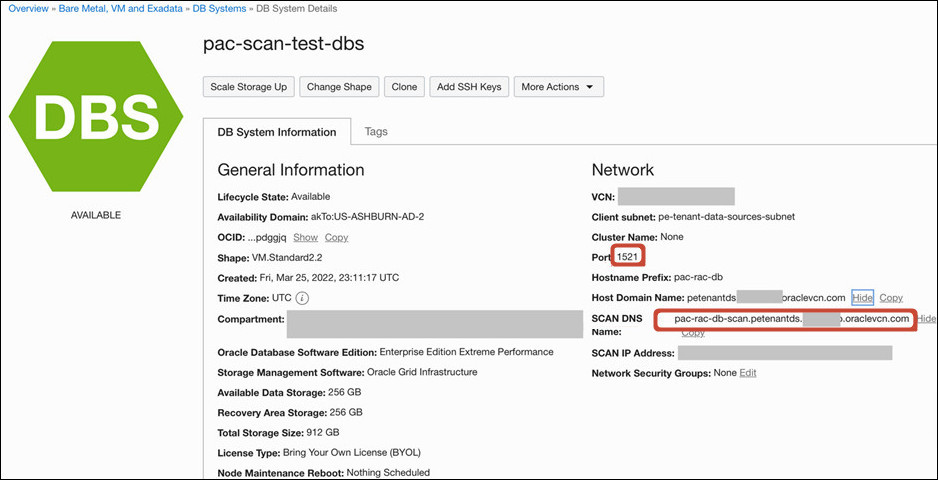
custcorp.com,example.com,myoacvcn.oraclevcn.com, and so on. - SCAN Host and Port: Specify host names such as
db01-scan.corp.example.com,prd-db01-scan.mycompany.com, and the port where the SCAN protocol connects, for example1521.
How Do I Connect?
You configure private access in two stages.
-
Stage 1) In Oracle Cloud Infrastructure Console, you set up a private access channel and register the data sources that require private access using their DNS domain name or SCAN host name and port.
When you set up (or edit) a private access channel you alter the configuration of your Oracle Analytics Cloud instance. Some users might experience a temporary disruption in service during the configuration process so Oracle recommends that you plan private access channel configuration on critical instances accordingly.
- Stage 2) In Oracle Analytics Cloud, you connect to the data source and analyze the data in the usual way.
For more guidance, see Typical Workflow to Set Up a Private Access Channel.
Supported Data Sources
Private access channels enable you to connect to private data source hosts. You can't use a private access channel to access any other type of private host. For example, you can't use private access channels to access private hosts that represent FTP servers, SMTP servers, printers , MapViewer configuration, or any other type of private host you might you use.
Limitations
- Configure the data source connection using the
Advanced Connection String option and connect
directly to the Oracle Database nodes, instead of SCAN.
For example:
(DESCRIPTION=(ENABLE=BROKEN) (ADDRESS_LIST=(LOAD_BALANCE=on)(FAILOVER=ON) (ADDRESS=(PROTOCOL=tcps)(HOST=<DB Node 1 FQDN Host Name>)(PORT=2484)) (ADDRESS=(PROTOCOL=tcps)(HOST=<DB Node 2 FQDN Host Name>)(PORT=2484))) (CONNECT_DATA= (SERVICE_NAME=<DB Service Name>)) (SECURITY=(SSL_SERVER_CERT_DN="CN=<DB Server Certificate DN>")))Where the distinguished name (DN) might look something like:
(SECURITY=(SSL_SERVER_CERT_DN="CN=host-example-scan.mysubnet.exadatainfrastr.oraclevcn.com"))The way you configure this connection string depends how many database hosts are active at the same time:-
If more than one database host is active at the same time, set
(LOAD_BALANCE=on)in the connection string above. -
If only one database host is active at a time, set
(LOAD_BALANCE=off)in the connection string. To optimize performance, include theADDRESSof the active database host first in theADDRESS_LIST.To find out which database host is active at any given time, refer to the documentation for your database. For example, for Oracle Database you can use V$INSTANCE.
-
- Configure an Oracle Connection Manager in front of SCAN and then configure a data source connection in Oracle Analytics Cloud that connects to the Oracle Connection Manager endpoint.
Frequently Asked Questions
Prerequisites for a Private Access Channel
Before you configure a private access channel, you need to know the domain names of the private DNS zones or SCAN host names you want Oracle Analytics Cloud to access, check that you deployed Oracle Analytics Cloud with Enterprise Edition, and verify you have the correct permissions.
If your Oracle Analytics Cloud is deployed with a public endpoint, you also need to know the VCN and subnet on Oracle Cloud Infrastructure that you want Oracle Analytics Cloud to use to access the private sources. If you deployed Oracle Analytics Cloud instance with a private endpoint, the private access channel automatically uses the same VCN and subnet you configured for the instance so you don't need to do step 3.
Typical Workflow to Set Up a Private Access Channel
If you want to set up a private access channel for an Oracle Analytics Cloud instance for the first time, follow these tasks as a guide.
| Task | Description | More Information |
|---|---|---|
| Understand prerequisites for a private access channel |
Make a list of the private data sources (DNS zones and SCAN host names) that you want Oracle Analytics Cloud to access through the private access channel and ensure you have the required permissions to set up the private access channel in Oracle Cloud Infrastructure. |
Prerequisites for a Private Access Channel |
|
Create an Oracle Analytics Cloud instance |
Deploy Oracle Analytics Cloud with Enterprise Edition. |
|
|
Configure a private access channel |
Use Oracle Cloud Infrastructure Console to configure a private access channel and list any data sources that Oracle Analytics Cloud must connect to privately (DNS zones and SCAN host names). Optionally, restrict outgoing traffic (egress) on the private access channel using one or more network security groups. |
|
| Create connections to private data sources |
Use Oracle Analytics Cloud to create a connection to the private data source. The way you create the connection depends on how you want to use the data source, that is, whether you want to build a visualization, analysis, pixel-perfect report, or semantic model. |
Connect to Data for Visualizations and Analyses |
|
Manage the data sources available through a private access channel |
Add, edit, or delete the private data sources that Oracle Analytics Cloud can access through the private access channel. Use the DNS zone or SCAN host name to identify your private data sources. |
Manage the Private Data Sources You Can Access on a Private Access Channel using the Console |
| Edit network details for a private access channel |
Change the VCN or subnet on Oracle Cloud Infrastructure that Oracle Analytics Cloud uses to access private data sources. Optionally, restrict traffic over the private access channel using network security groups. |
Edit Network Details for a Private Access Channel using the Console |
|
Delete a private access channel |
Delete a private access channel that you configured for Oracle Analytics Cloud but don't need anymore. |
Configure a Private Access Channel
You can configure a private access channel using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Verb: manage
Resource Type:
virtual-network-family
Verb: read
Resource Type: compartment,
compartments
Resource Type: work-requests
(required for SCAN host configuration)
To learn about other, more detailed access policy options, see Prerequisites for a Private Access Channel.
Configure a Private Access Channel using the Console
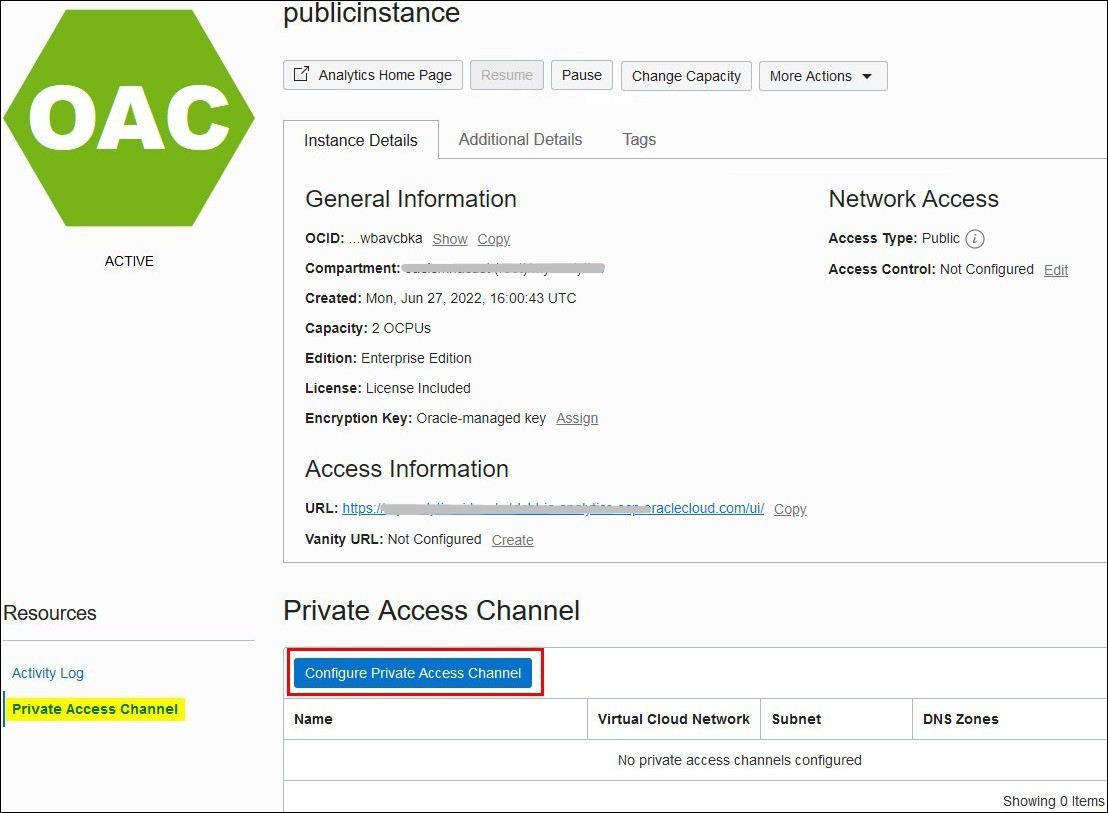
You can use Oracle Cloud Infrastructure Console to configure a private access channel for your Oracle Analytics Cloud instance.
When you set up a private access channel you alter the configuration of your Oracle Analytics Cloud instance. Some users might experience a temporary disruption in service during the configuration process so Oracle recommends that you plan private access channel configuration activities on critical instances accordingly.
Configure a Private Access Channel using the REST API
You can use the CreatePrivateAccessChannel operation to
set up a private access channel for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Configure a Private Access Channel using the Command Line
You can use the analytics-instance
create-private-access-channel command to set up a private access
channel for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command:
Edit a Private Access Channel
You can edit a private access channel using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Verb: manage
Resource Type:
virtual-network-family
Verb: read
Resource Type: compartment,
compartments
Resource Type: work-requests
(required for SCAN host configuration)
To learn about other, more detailed access policy options, see Prerequisites for a Private Access Channel.
Edit Network Details for a Private Access Channel using the Console
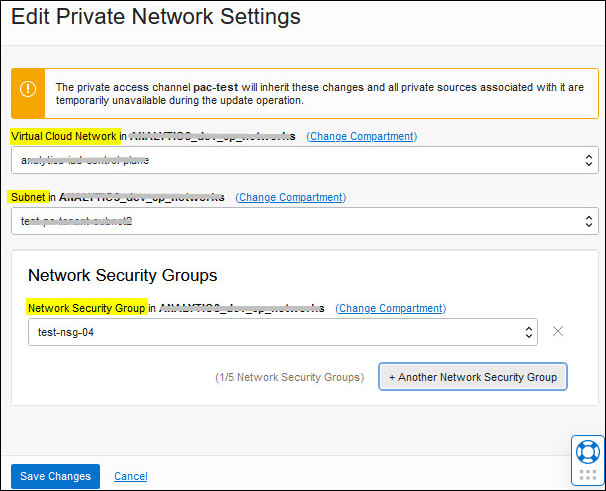
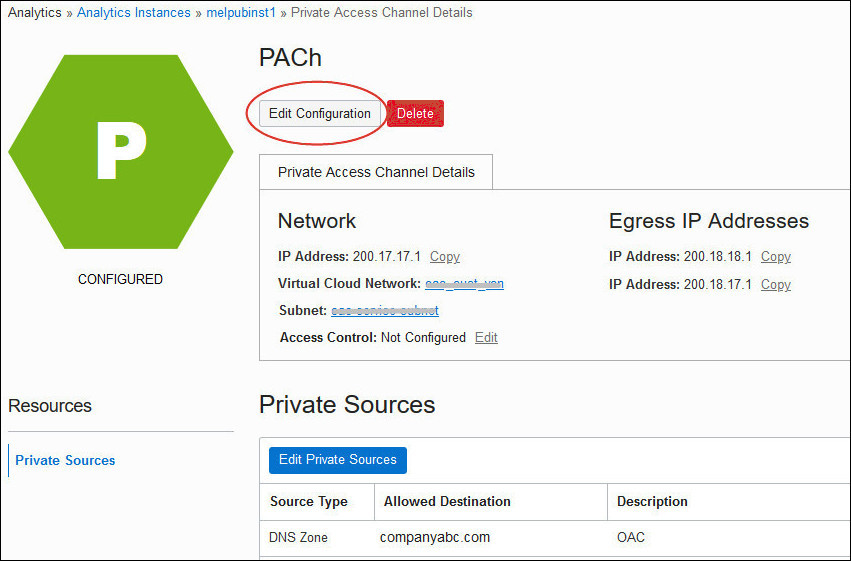
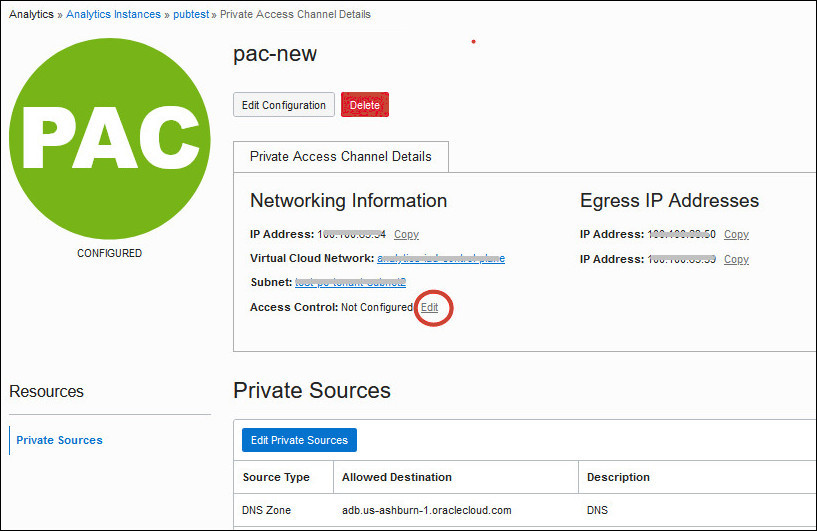
If you deployed your Oracle Analytics Cloud instance with a public endpoint, you can change the VCN, subnet and network security groups on Oracle Cloud Infrastructure that Oracle Analytics Cloud uses to access private sources.
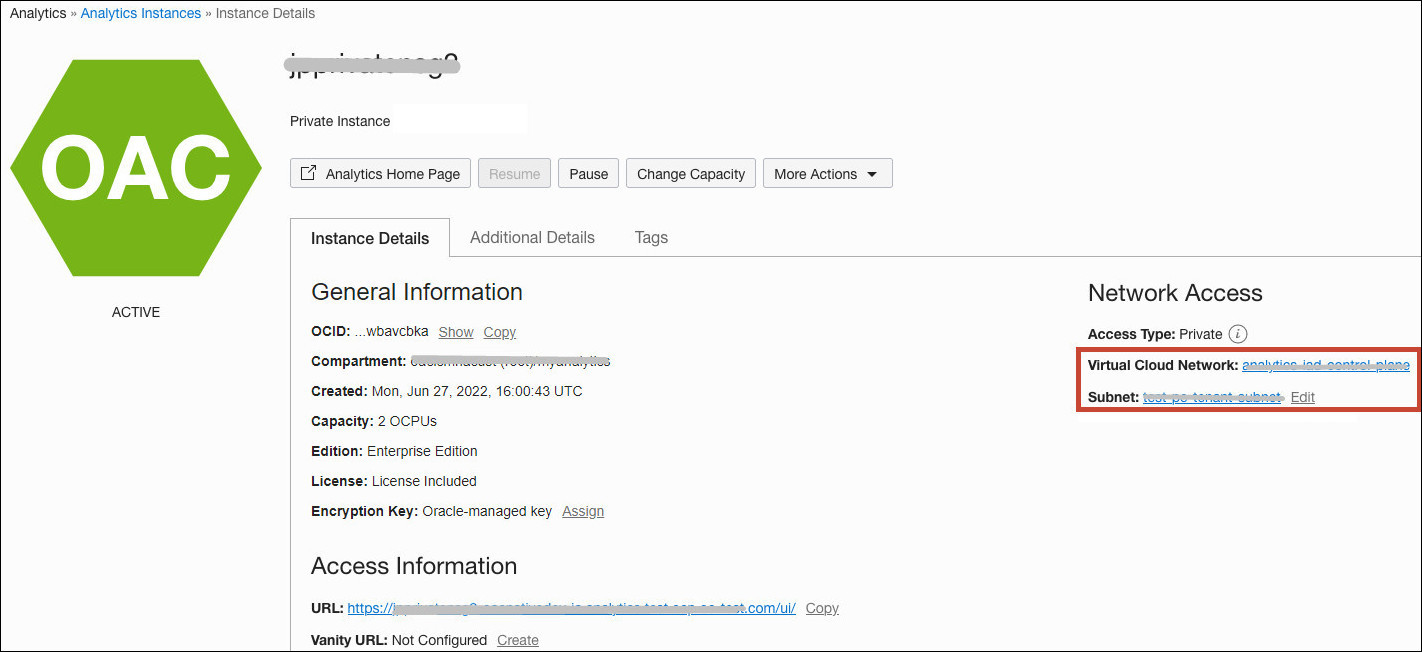
When you deploy Oracle Analytics Cloud with a private endpoint, the private access channel uses the same VCN, subnet, and network security groups you configured for the private endpoint. To edit network settings for both the private endpoint and private network channel, see Change the VCN or Subnet Used to Access a Private Endpoint.
Changing the VCN or subnet impacts any private data sources that you configured for this private access channel. You must ensure that the new network configuration provides a network route to these sources.
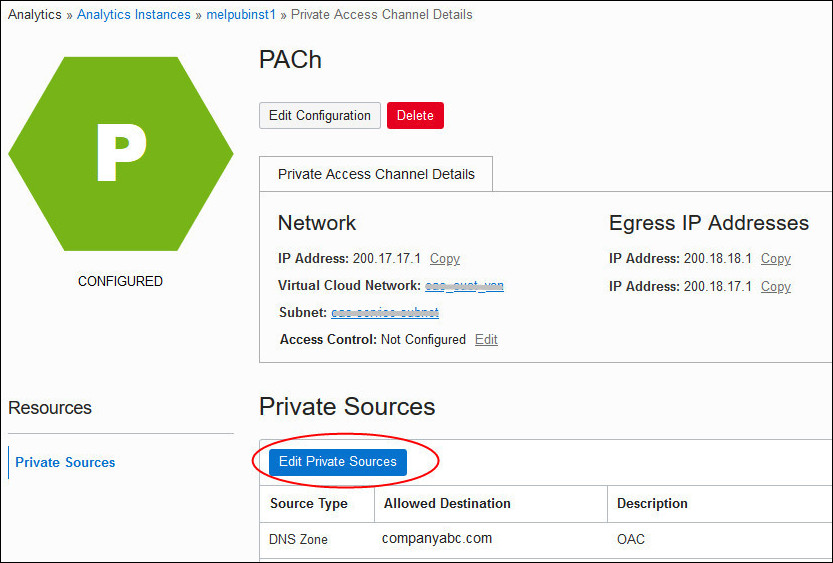
Manage the Private Data Sources You Can Access on a Private Access Channel using the Console
You can add, edit, or delete the DNS zones and SCAN hosts of private sources available through the private channel at any time.
Edit a Private Access Channel using the REST API
You can use the UpdatePrivateAccessChannel operation to
edit a private access channel that you configured for an Oracle
Analytics Cloud instance.
You can manage the DNS zones and SCAN hosts accessible through the private access channel and, if your Oracle Analytics Cloud has a public endpoint, you can change the VCN, subnet, and network security groups that the private access channel uses to access the private data sources.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Edit a Private Access Channel using the Command Line
You can use the analytics-instance
update-private-access-channel command to edit a private access
channel that you configured for an Oracle
Analytics Cloud instance.
You can manage the DNS zones and SCAN hosts accessible through the private access channel and, if your Oracle Analytics Cloud has a public endpoint, you can change the VCN, subnet, and network security groups that the private access channel uses to access the private data sources.
Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command:
Delete a Private Access Channel
You can delete a private access channel using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Verb: manage
Resource Type:
virtual-network-family
Verb: read
Resource Type: compartment,
compartments
To learn about other, more detailed access policy options, see Prerequisites for a Private Access Channel.
Delete a Private Access Channel using the Console
You can delete a private access channel that you configured for Oracle Analytics Cloud but don't need anymore.
Delete a Private Access Channel using the REST API
You can use the DeletePrivateAccessChannel operation to
delete a private access channel for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Delete a Private Access Channel using the Command Line
You can use the analytics-instance
delete-private-access-channel command to delete a private access
channel for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command:
Use Network Security Groups to Control Access
You can restrict incoming and outgoing traffic to Oracle Analytics Cloud through ingress and egress rules that you define in network security groups.
Topics
- About Network Security Groups and Security Lists
- About Using Network Security Groups with Oracle Analytics Cloud
- Prerequisites for Network Security Groups
- Manage Egress Access Rules for a Public Endpoint using the Console
- Manage Ingress and Egress Access Rules for a Private Endpoint using the Console
- Top FAQs for Network Security Groups
About Network Security Groups and Security Lists
The Networking service in Oracle Cloud Infrastructure (OCI) offers two virtual firewall features to control traffic at the packet level: network security groups and security lists.
- Network security groups (NSGs): Act as a virtual firewall for OCI resources such as Oracle Analytics Cloud. An NSG consists of a set of ingress and egress security rules that apply only to a set of VNICs of your choice in a single VCN. To learn more about NSGs and how to manage ingress and egress security rules, see Network Security Groups.
- Security lists: The original type of virtual firewall offered by the Networking service. See Security Lists.
Either option or a combination of these two features can be used. See Comparison of Security Lists and Network Security Groups .
About Using Network Security Groups with Oracle Analytics Cloud
You can use network security groups (NSGs) to define ingress and egress security rules that restrict traffic to and from Oracle Analytics Cloud. This topic describes ingress and egress scenarios for Oracle Analytics Cloud.
About Ingress Scenarios for Oracle Analytics Cloud
- Public endpoint: Use access control rules to control incoming traffic. See Control Incoming Traffic to Public Endpoint (Ingress).
- Private endpoint: Use a union of ingress rules to control
incoming traffic from:
- NSGs for the private Oracle Analytics Cloud instance. See Control Incoming Traffic to Private Endpoint (Ingress).
- Security lists for the subnet.
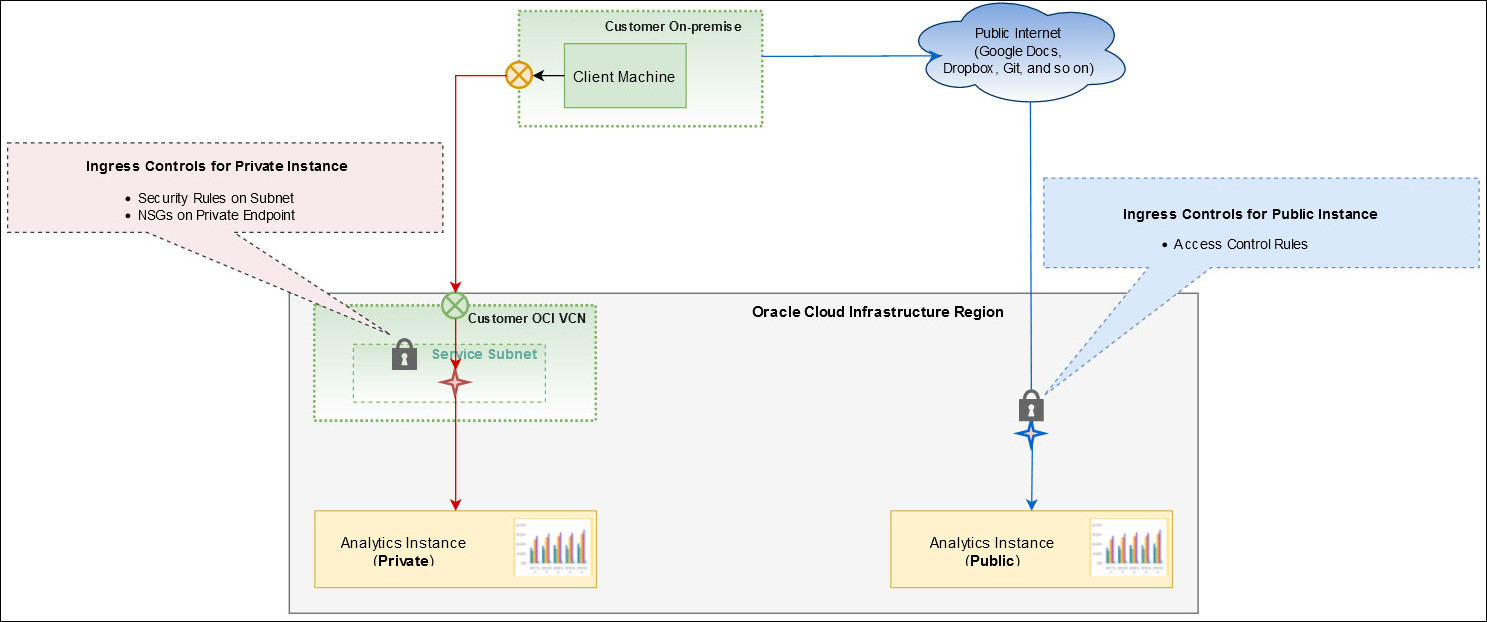
About Egress Scenarios for Oracle Analytics Cloud
The way you manage egress depends on the data source you want to access from Oracle Analytics Cloud.
- Publicly accessible data sources: Oracle Analytics Cloud can egress to any data source accessible on the public internet.
- Private data sources accessible through a private access
channel: Use a union of egress rules to control outgoing traffic
from:
- NSGs for the private access channel. See Control Outgoing Traffic to Private Endpoint (Egress).
- Security lists for the private access channel subnet.
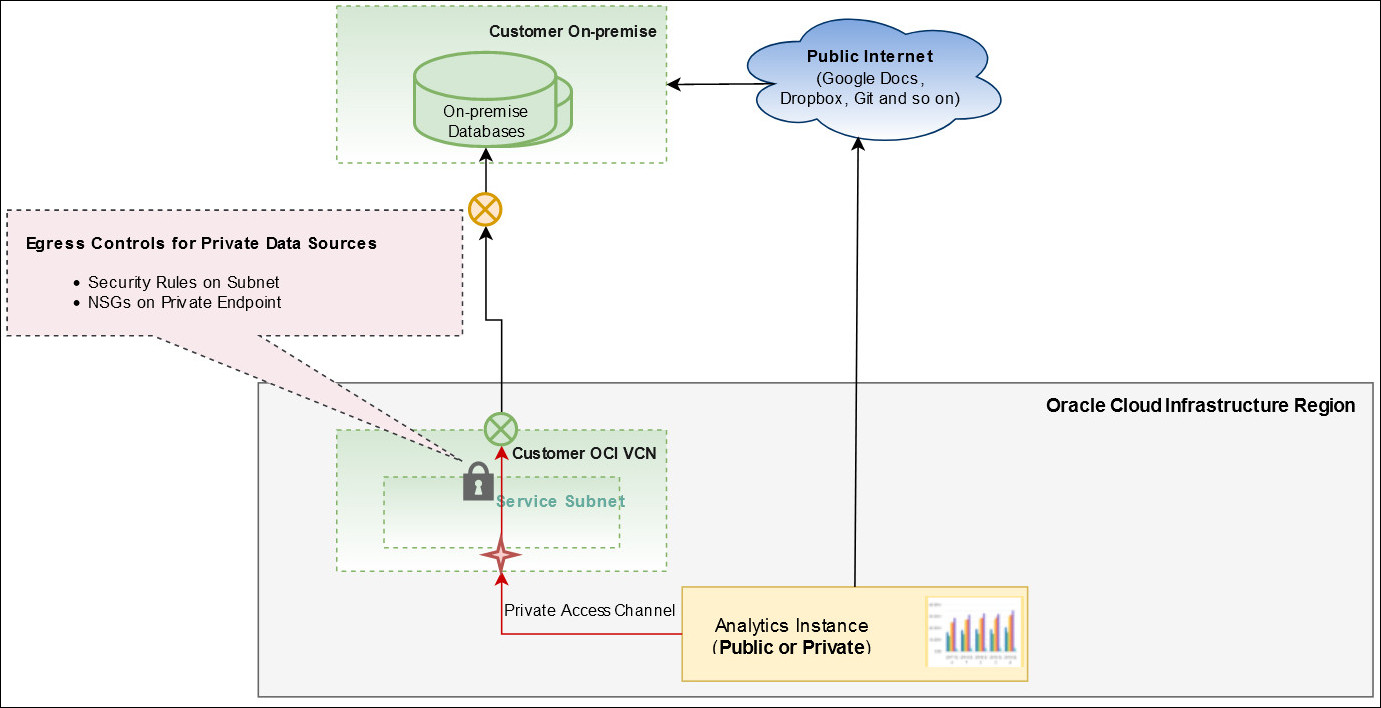
Manage Egress Access Rules for a Public Endpoint using the Console
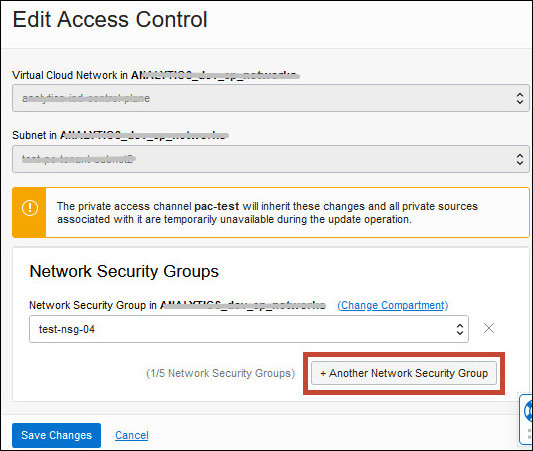
If you deployed Oracle Analytics Cloud with a public internet accessible endpoint and you have private data sources that Oracle Analytics Cloud connects to over a private access channel, you can use egress rules that you define in network security groups to restrict outgoing traffic through the channel. You can add up to five network security groups.
Any network security groups that you want to use must be in the same VCN as the private access channel.
Prerequisites for Network Security Groups
Before you configure network security groups (NSGs) for your Oracle Analytics Cloud instances, complete the required prerequisites.
VCN and Subnet Configuration
Configure the VCN you want to use with or without public access. See OCI VCN with Public and Private Subnet or OCI VCN with Only Private Subnet.
Ensure there's at least 4 IP addresses available in the subnet that you want Oracle Analytics Cloud to use.
Network Security Group Configuration
Configure all the NSGs you want to use in the same VCN as your Oracle Analytics Cloud instance. See Working with Network Security Groups.
Add ingress rules to the NSG to control inbound traffic to a private Oracle Analytics Cloud instance.
Add egress rules to the NSG to control outbound traffic from a public or private Oracle Analytics Cloud instance going to private data sources (through a private access channel).
Additional Policy Requirements
ALLOW GROUP <ANALYTICS ADMIN> TO USE network-security-groups in TENANCY
Manage Ingress and Egress Access Rules for a Private Endpoint using the Console
If you deployed Oracle Analytics Cloud with a private endpoint, you can restrict incoming traffic (ingress) and outgoing traffic through private access channels (egress) using predefined network security groups that contain one or more ingress or egress rules.
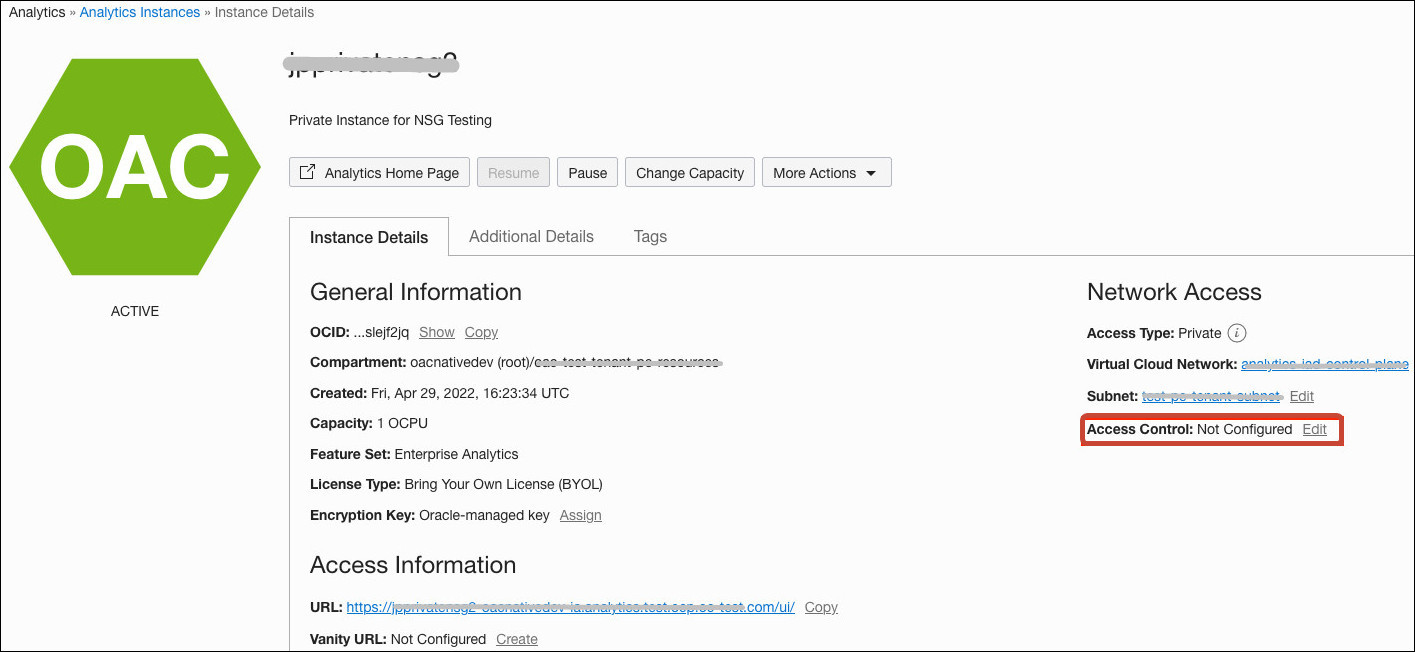
You define the network security groups that you want your Oracle Analytics Cloud instance to use on the Instance Details page. Ingress rules defined in the network security groups are applied to incoming traffic. If you use a private access channel to connect to private data sources, egress rules in the network security groups are applied to outgoing traffic on this private access channel.
Any network security groups you want to use must be in the same VCN as your Oracle Analytics Cloud instance (and the private access channel).
Federate with Oracle Identity Cloud Service Manually
In most cases, Oracle Analytics Cloud is automatically federated with the primary Oracle Identity Cloud Service instance associated with your tenancy. If you want to federate Oracle Analytics Cloud with a secondary Oracle Identity Cloud Service instance or your tenancy is a government region where federation isn't set up automatically, you must federate with Oracle Identity Cloud Service manually.
![]() This topic applies only to cloud accounts that don't use identity domains. See
Set Up Users.
This topic applies only to cloud accounts that don't use identity domains. See
Set Up Users.
The way you do this depends whether your Oracle Identity Cloud Service includes the COMPUTEBAREMETAL application. If a COMPUTEBAREMETAL application doesn’t exist in your tenancy, you must perform some additional steps to set up a trusted application that you can use.
Once set up, select the new Oracle Identity Cloud Service provider before you sign-in to Oracle Cloud and then create your Oracle Analytics Cloud instance. The new Oracle Analytics Cloud instance will use the federated Oracle Identity Cloud Service that you're signed-in with. You can't reconfigure Oracle Analytics Cloud to use a different Oracle Identity Cloud Service later on.
Set Up a Custom Vanity URL
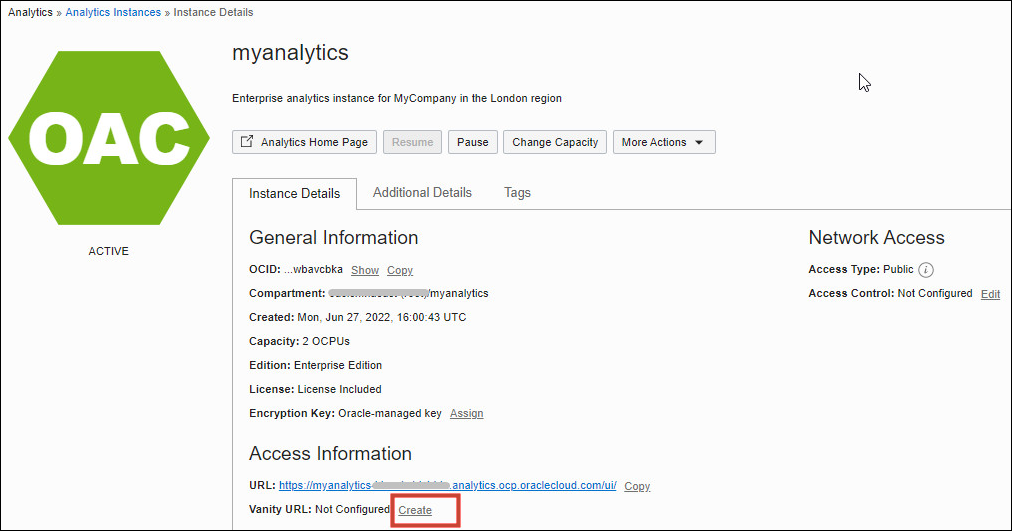
You can configure a custom vanity URL for your Oracle Analytics Cloud instance.
Topics:
About Vanity URLs
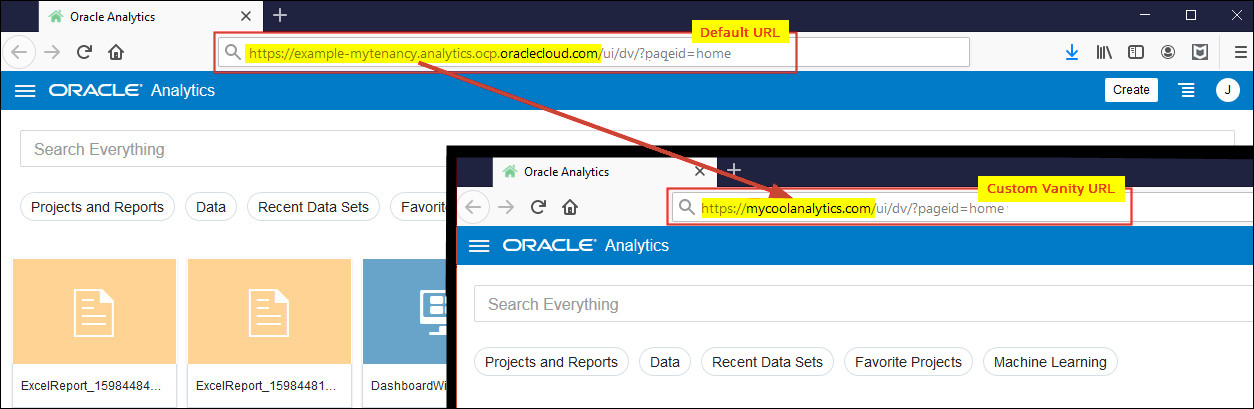
A vanity URL is a unique, customized web address that's branded for marketing purposes and helps users remember and find your web site. If you want to customize the user login experience for Oracle Analytics Cloud, you can use your own vanity URL instead of the default URL that Oracle provides.
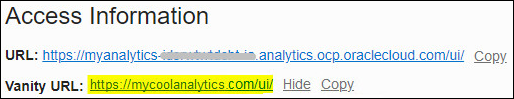
These examples show standard URL formats for Oracle Analytics Cloud and a sample vanity URL that you might use instead:
-
Standard URLs:
https://example-mytenancy-<regionid>.analytics.ocp.oraclecloud.com/uihttps://example-mytenancy.analytics.<regionid>.ocp.oraclecloud.com/ui
-
Vanity URL:
https://mycoolanalytics.com/ui
Typical Workflow to Set Up a Vanity URL
If you want to set up a vanity URL for an Oracle Analytics Cloud instance for the first time, follow these tasks as a guide.
| Task | Description | More Information |
|---|---|---|
| Understand prerequisites for a vanity URL |
Obtain the custom domain name and the required security certificates before you start. |
Prerequisites for a Vanity URL |
|
Deploy Oracle Analytics Cloud |
Deploy Oracle Analytics Cloud with a public or private endpoint. | |
|
Configure a vanity URL |
Use Oracle Cloud Infrastructure Console to configure a vanity URL. |
|
|
Update security certificates for the vanity domain |
If the security certificate, private key file, or certificate chain associated with your vanity domain expires or changes you can upload new details. |
|
|
Delete a vanity URL |
Delete a vanity URL that you configured for Oracle Analytics Cloud but don't need anymore. |
Prerequisites for a Vanity URL
Before you configure a vanity URL for an Oracle Analytics Cloud instance you need to know the custom domain name and valid certificate for the domain.
Configure a Vanity URL
You can configure a vanity URL using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Configure a Vanity URL using the Console
You can use Oracle Cloud Infrastructure Console to configure a vanity URL for your Oracle Analytics Cloud instance.
Configure a Vanity URL using the REST API
You can use the CreateVanityUrl operation to set up a
vanity URL for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Update Certificates for a Vanity URL
You can update the security certificates associated with your vanity URL using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Update Certificates for a Vanity URL using the Console
If the security certificate, private key file, or certificate chain associated with your vanity domain expires or changes you can upload new details using the Console.
Update Certificates for a Vanity URL using the REST API
You can use the UpdateVanityUrl operation to update
security certificates for the vanity URL that you configured for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Update Certificates for a Vanity URL using the Command Line
You can use the analytics-instance update-vanity-url
command to update security certificates for the vanity URL that you configured for
an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command:
Delete a Vanity URL
You can delete a vanity URL using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Delete a Vanity URL using the Console
You can delete a vanity URL that you configured for Oracle Analytics Cloud but don't need anymore.
- In Oracle Cloud
Infrastructure Console, click
 in the top left corner.
in the top left corner. - Click Analytics & AI. Under Analytics, click Analytics Cloud.
- Select the compartment that contains the Oracle Analytics Cloud instance you're looking for.
- Click the name of the instance you want to edit.
- On the Instance Details page, click More Actions and then select Remove Vanity URL.
- Click Remove to confirm.
Delete a Vanity URL using the REST API
You can use the DeleteVanityUrl operation to delete the
vanity URL configured for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Encrypt Sensitive Information
You can configure custom encryption keys for your Oracle Analytics Cloud instances or let Oracle manage data encryption for you.
Topics:
About Encryption in Oracle Analytics Cloud
Oracle Analytics Cloud provides two data encryption options:
- Oracle-managed encryption keys
- Customer-managed encryption keys
About Oracle-managed Encryption Keys
By default, Oracle manages encryption of data within Oracle Analytics Cloud using Oracle-managed keys. This doesn't include data in other platforms under your direct control. For example, data stored in cloud databases or on-premises databases that Oracle Analytics Cloud connects to.
About Customer-managed Encryption Keys
Optionally, you can use Vault services in Oracle Cloud Infrastructure to create and manage your own encryption keys for Oracle Analytics Cloud. Your customer-managed keys are used to encrypt Oracle Analytics Cloud data such as file-based datasets, any data in datasets that's configured for caching, and credentials used to connect to your data sources.
To use custom encryption, your Oracle Analytics Cloud instance must be deployed with Enterprise Edition. Custom encryption isn't available on Oracle Analytics Cloud instances deployed with Professional Edition.
To configure custom encryption, you must have permissions to manage the Oracle Analytics Cloud instance, create and assign encryption keys, and access Oracle Cloud Infrastructure Object Storage. See Prerequisites for Custom Encryption.
Caution:
The customer-managed encryption key is stored in Oracle Cloud Infrastructure Vault, external to your Oracle Analytics Cloud instance. Deleting or disabling a customer-managed key makes your content within Oracle Analytics Cloud unreadable for everyone, including Oracle, and your Oracle Analytics Cloud instance will be inaccessible.
About Rotating Customer-managed Encryption Keys
Oracle recommends that you rotate your custom encryption key from time-to-time to maintain security compliance. After rotating your custom encryption key in Oracle Cloud Infrastructure Vault, you must assign the new key version to your Oracle Analytics Cloud instance.
- In Oracle Cloud Infrastructure Vault, rotate the key. See Rotate a master encryption key.
- In your Oracle Analytics Cloud instance, assign the new key version. See Rotate the custom encryption key.
Typical Workflow to Manage Encryption
If you want Oracle Analytics Cloud to use a custom encryption key, follow these tasks as a guide.
| Task | Description | More Information |
|---|---|---|
| Understand prerequisites for custom data encryption |
Set up a vault and create one or more master encryption keys before you start. |
Prerequisites for Custom Encryption |
|
Assign a custom encryption key to your Oracle Analytics Cloud instance |
Use Oracle Cloud Infrastructure Console to assign the custom encryption key to your Oracle Analytics Cloud instance. If the Oracle Analytics Cloud instance doesn’t exist yet and your custom encryption key is ready, you can create the instance with custom encryption from the start. See Create a Service. |
|
|
Rotate a custom encryption key and update your Oracle Analytics Cloud instance |
Rotate your existing encryption keys periodically to maintain security compliance, and then update your Oracle Analytics Cloud instance to use the latest version. If necessary, you can change to a different encryption key. |
|
|
Remove a custom encryption key from your Oracle Analytics Cloud instance |
Remove an encryption key that you configured for Oracle Analytics Cloud but don't need anymore. Use Oracle-managed keys instead. |
Prerequisites for Custom Encryption
Before you configure custom encryption for your Oracle Analytics Cloud instance, you must set up a vault with one or more master encryption keys, and ensure that you have all the required permissions.
Assign a Custom Encryption Key
You can assign a custom encryption key to an existing Oracle Analytics Cloud instance using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Verb: use
Resource Type:
key-delegate
Verb: read
Resource Type: vaults,
keys
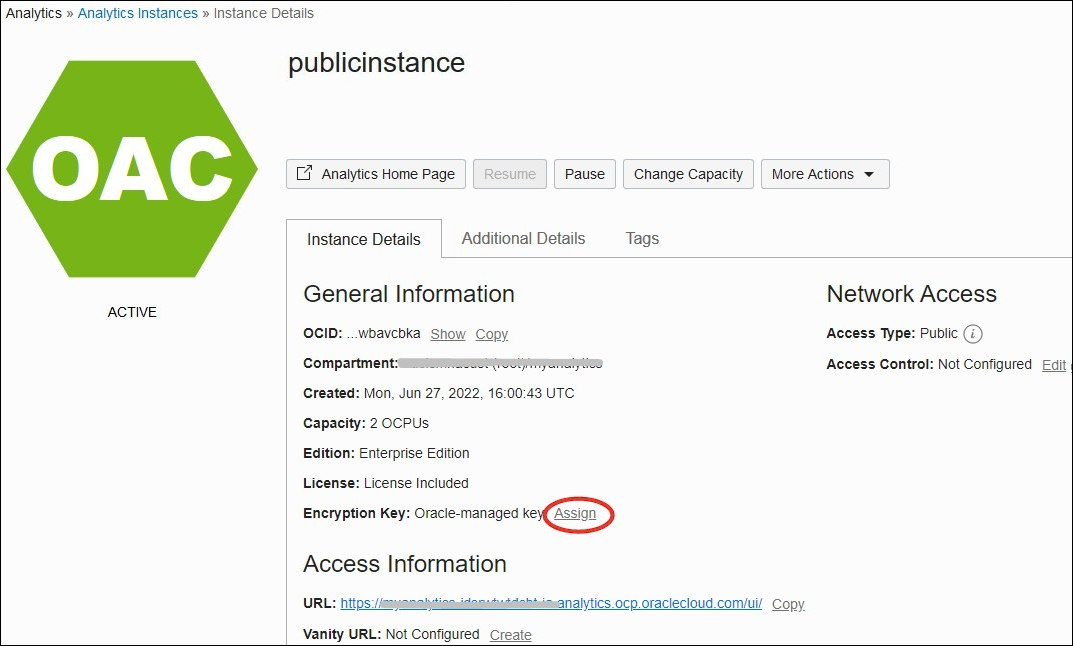
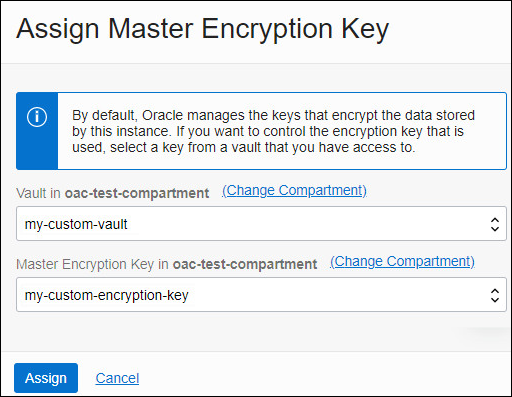
Assign a Custom Encryption Key using the Console
You can use Oracle Cloud Infrastructure Console to assign a custom encryption key for your Oracle Analytics Cloud instance.
Assign a Custom Encryption Key using the REST API
You can use the SetKmsKey operation to assign a custom
encryption key for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
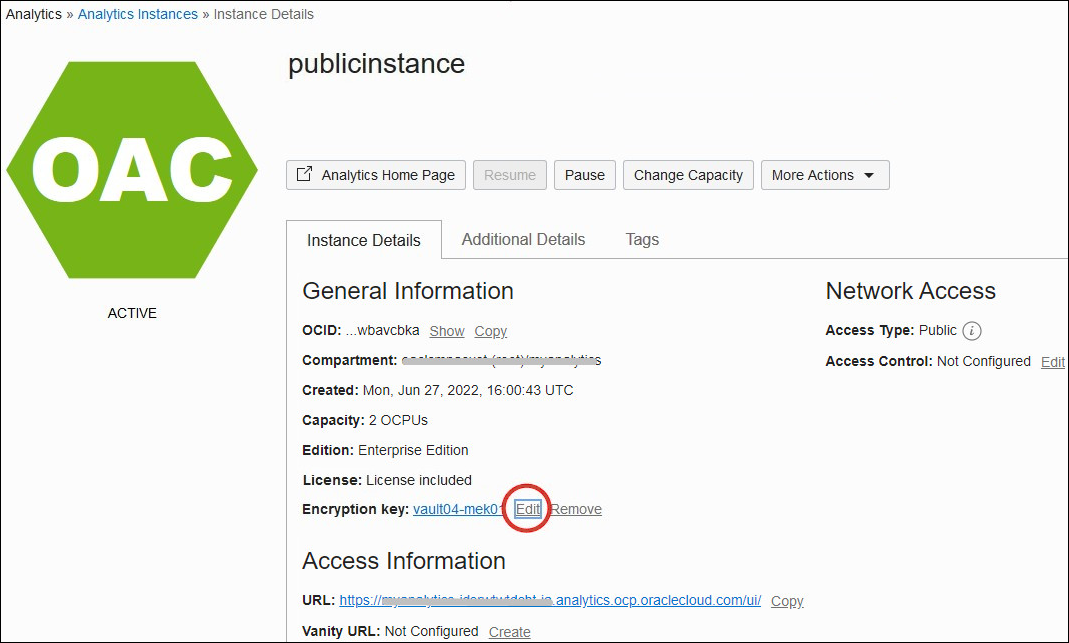
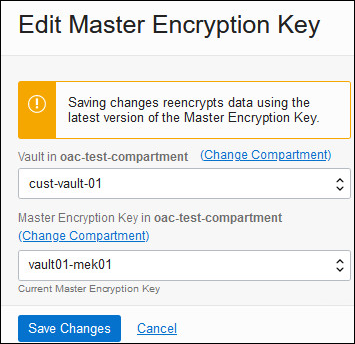
Rotate or Change the Custom Encryption Key
Each time you rotate your custom encryption key (or have to change to a different custom encryption key), you must update your Oracle Analytics Cloud instance. You can update the custom encryption key for an Oracle Analytics Cloud instance using the Console, API, or command line.
Each master encryption key is automatically assigned a key version. When you rotate a key, the Vault service generates a new key version. Periodically rotating keys limits the amount of data encrypted or signed by a single key version. If a key is ever compromised, key rotation reduces the risk. Each key’s unique identifier (OCID), remains the same across rotations, but the key version lets the Vault service seamlessly rotate keys to meet any security compliance requirements you might have. Although Oracle Analytics Cloud doesn't use an older key version for encryption after you rotate a key, older key versions remain available to decrypt any Oracle Analytics Cloud data that it previously encrypted.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Verb: use
Resource Type:
key-delegate
Verb: read
Resource Type: vaults,
keys
Rotate or Change the Custom Encryption Key using the Console
Oracle recommends that you rotate your custom encryption key from time-to-time to maintain security compliance. After rotating your encryption key, you can use the Console to assign the new key version to your Oracle Analytics Cloud instance.
If for any reason you need to change to a different encryption key, you can do this from the Console too.
Rotate or Change the Custom Encryption Key using the REST API
You can use the SetKmsKey operation to rotate an
existing encryption key (refresh the same key OCID) or change the encryption key (configure
a new key OCID) for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Rotate or Change the Custom Encryption Key using the Command Line
You can use the analytics-instance set-kms-key command to
rotate an existing encryption key (refresh the same key OCID) or change the
encryption key (configure a new key OCID) for an Oracle
Analytics Cloud instance.
Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command:
Remove a Custom Encryption Key
You can remove a custom encryption key at any time and let Oracle manage data encryption for you. You can remove the key using the Console, API, or command line.
Required IAM Policy
Verb: manage
Resource Type:
analytics-instance,
analytics-instances
Custom Permission:
ANALYTICS_INSTANCE_MANAGE
See About Permissions to Manage Oracle Analytics Cloud Instances.
Verb: use
Resource Type:
key-delegate
Verb: read
Resource Type: vaults,
keys
Remove a Custom Encryption Key using the Console
You can remove a custom encryption key that you configured for Oracle Analytics Cloud but don't need anymore.
Remove a Custom Encryption Key using the REST API
You can use the SetKmsKey operation to remove a custom
encryption key configured for an Oracle
Analytics Cloud instance. To remove the current key, specify an empty string for the
kmsKeyId.
Refer to the Oracle Cloud Infrastructure REST API Reference for information about how to use this operation:
Remove a Custom Encryption Key using the Command Line
You can use the analytics-instance set-kms-key command to
remove a custom encryption key configured for an Oracle
Analytics Cloud instance. To remove the current key, specify an empty string for the
kmsKeyId.
Refer to the Oracle Cloud Infrastructure CLI Command Reference for information about how to use this command: