Onboarding External KMS
Steps to onboard users to External Key Management System.
The External KMS onboarding process includes details about setting up network components, setting up new user account, providing user permissions, configuring private endpoint, and configuring network policies and IAM policies for accessing vault and keys.
The following diagram is a workflow showing the steps involved in onboarding the External KMS feature:
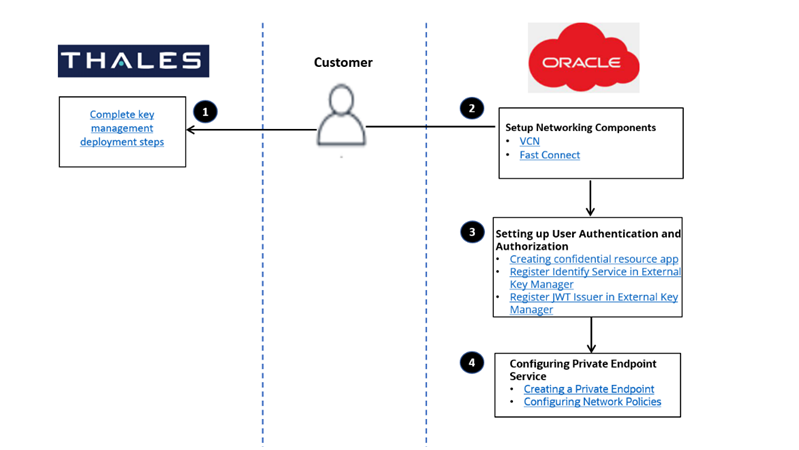
The External KMS onboarding process involves a series of steps to be completed. You must complete these steps to set up your network configuration.
- Deploying Cipher Trust Manager
- Setting up Networking Components
- Setting up FastConnect
- Setting up TLS Connectivity using FQDN
- Setting up TLS Connectivity using Static IP Address
- Setting up Authentication and Authorization
- Setting up user authentication and authorization
- Configuring Private Endpoint Service
Deploying Cipher Trust Manager
Deploy Thales Cipher Trust Manager
To set up Cipher Trust Manager, as a prerequisite you must first complete the Thales CipherTrust Manager (CM) deployment steps.
For more information about Thales CM deployment, see CipherTrust Manager Deployment